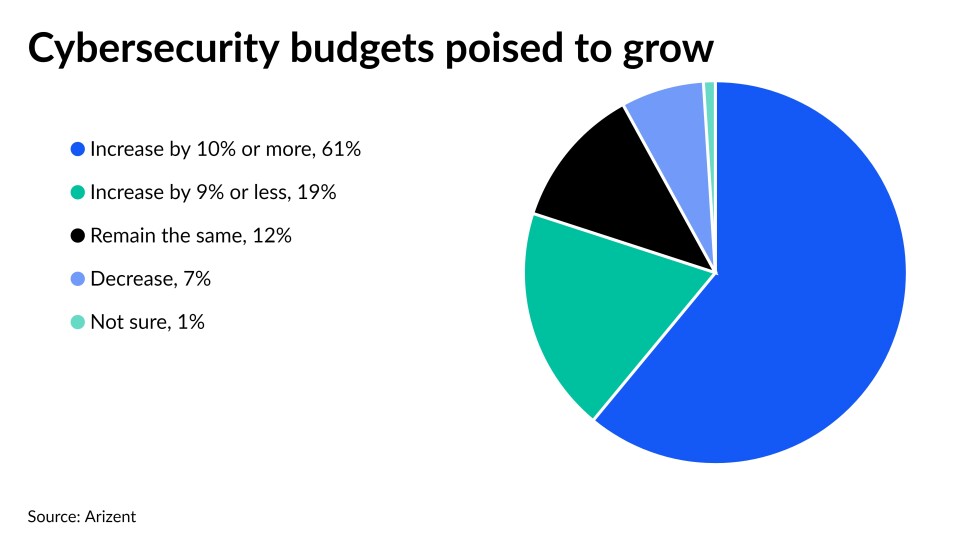
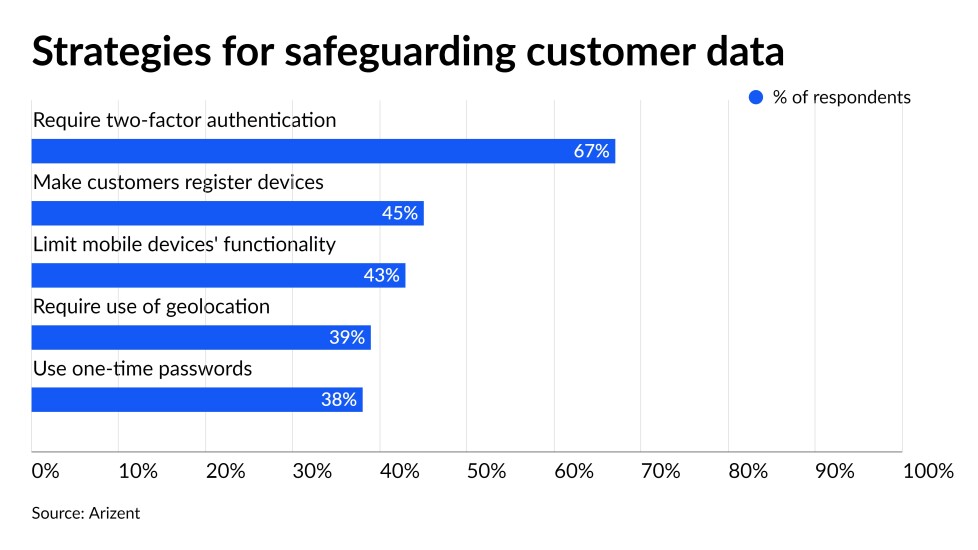
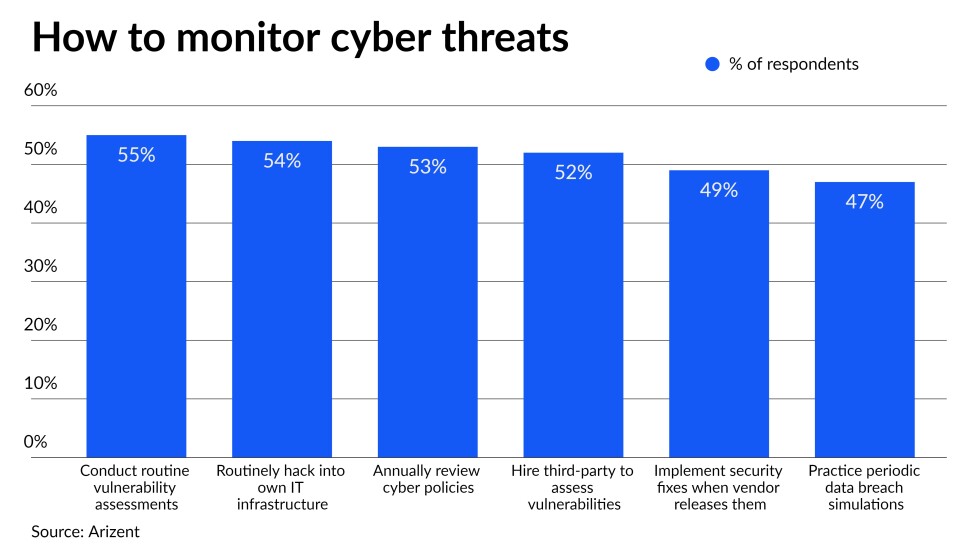
Many banks plan to spend big to protect their data and computer systems in the coming year, potentially leaving behind others that are responding less aggressively to cyberattacks.
That was one of the findings of a new survey conducted by Arizent — the publisher of American Banker and several other financial services publications — of financial industry executives involved in or aware of their organization’s cybersecurity policies and practices. It also highlighted the widening use of two-factor authentication, the broad range of methods that some banks use to test their security and the many modes of attack cyberthieves and fraudsters have at their disposal.
A full report on the results,
Of the 192 survey respondents to the survey, about 100 worked in banking. Arizent collected feedback between late November and late December. Summarized here are four key findings from the report and its conclusion, as well as commentary from outside experts.