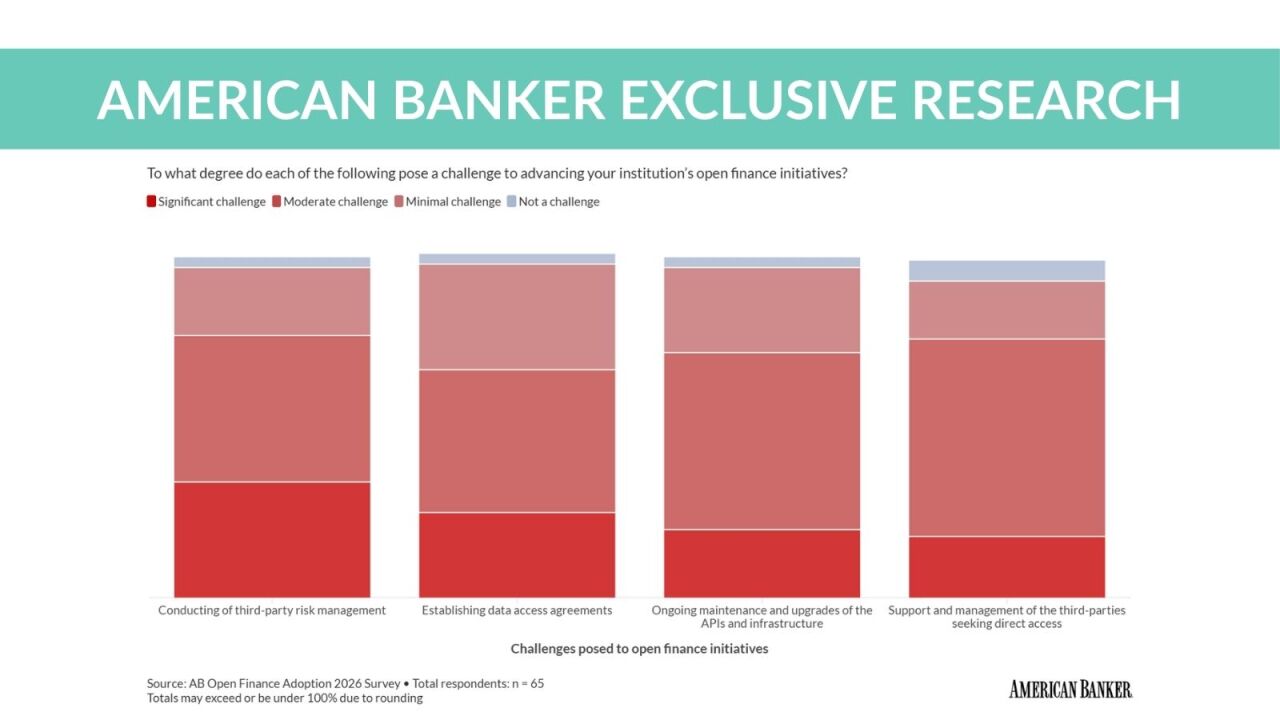
Before reports of the data breach at Saks Fifth Avenue, Saks OFF 5th, and Lord & Taylor fade from the news cycle, there's one detail that should alarm merchants, card issuers and consumers — and sets a tone for future data breaches.
These days, many consumers have already experienced account and identity theft and are familiar with the recourses available to them. As a result, their details are less valuable to fraudsters, who are not as interested in paying for credentials they can no longer exploit.

The masterminds of the Saks/Lloyds data breach take a new approach that could rekindle the market for stolen credentials. The incident was
The cybersecurity intelligence firm Gemini Advisory estimates the attackers had access for almost a year, with the initial compromise dating back at least as far as May 2017. As is usual with such breaches, the affected companies were not explicitly identified by the hackers, but researchers were able to confirm that the leaked card numbers were connected by recent purchases at one of the chains.
Also following standard protocol, only a small portion of the data is so far up for sale, with more expected to be released in batches over the next few months. From analysis of what’s been posted, it seems the breach mainly affects shoppers in New York and New Jersey, although at least three Canadian outlets are included in the list.
The Joker’s Stash gang, also known as Fin7, have made a name for themselves selling large quantities of stolen card data on the dark web. They have been linked to card data breaches at Hilton Hotels, Jason’s Deli and Sonic Drive-In.
They also engage in some rather complex approaches to keeping their network of underground sales sites hidden from prying eyes while maintaining ease of use for their “customers”, with users given multiple unique URLs to use to reach the service, each redirecting communications to the real website hidden in the Tor network.
Exactly how the breach happened remains rather shadowy, although a Gemini Advisory representative told
Such carefully-crafted attacks focus on high-powered individuals with elevated access within a corporate network, tricking them into either revealing login credentials or visiting malware-infected web pages which open backdoors into their systems.
Thus, all of the protections the payment card industry is putting in place at the point of sale amount to very little. This is a data breach that could not have been prevented by increased use of chip-and-PIN, tokenization, biometrics or machine learning.
The next step for card issuers and retailers will be a bit more familiar. Now that the card data is up for sale, it is likely to be used to print counterfeit cards and use them to purchase high-value, easily-fenced computer hardware, targeting big box stores which haven’t yet implemented EMV to protect card users from this kind of fraud.