The network security of banks and other financial institutions are notable for their stability. However, the vendors that they utilize to handle and process data do not always have an equally stringent security posture that prevents hacker exploitation. Therefore, there are still greater risks in existence for these institutions and their networks.
As a result of these risks, it is expected that cyber spending will grow exponentially.
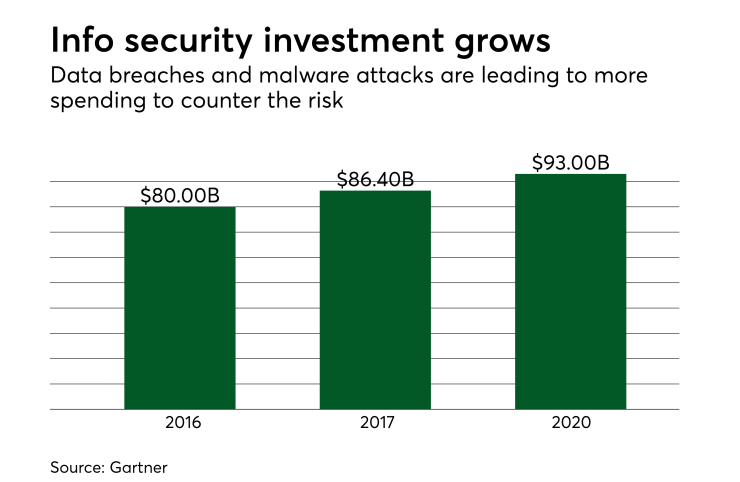
Already, the financial industry’s spending on information security has globally grown to 67%. With the increased demand for heightened security and the increased costs, there will also be a growth in attacks from nation-state actors. Attacks from nation-state actors have risen in regards to the number of nation-states engaged in financially motivated cybercrime. As a result, more than 30 new countries are investing in the development of offensive cyber capabilities.
However, all users are still vulnerable as these attacks can target a variety of platforms.
There are nine various vectors of attack that are the most common: business email compromise (BEC), mobile banking, automated teller machine (ATM) attacks, social engineering, distributed denial of service (DDOS) attacks, ransomware, automation, attacks on smaller and unsecured banks to access larger banks, and hybrid attacks.
Business email compromise is when a hacker tricks employees into transferring large amounts of money into the desired accounts. The hacker accomplishes this by posing as a high-level executive or manager. This form of attack can be difficult for financial institutions to catch because the transaction is submitted through the proper channels by legitimate and authorized people.
Mobile Banking is becoming a main form of interaction between the bank and customers as customers can deposit checks, transfer money, pay bills, and more all with a few clicks. However, mobile banking also connects millions of new devices to the network and this provides a new vector of attack for hackers. According to a study conducted by Kaspersky Labs, this vulnerability has been drastically exploited in recent years as mobile malware attacks led by mobile banking trojans more than tripled in 2016.
ATM attacks have risen as hackers have begun targeting the machines. These ATMs come from the banks’ core networks. When they're attacked, the systems that manage the ATM network are therefore compromised instead of the machine itself.
Social engineering is essentially the use of deception to manipulate individuals into revealing personal information that can then be used for fraudulent purposes. Social engineers are becoming more sophisticated with their attacks through pretexting.
They do this by engaging in back and forth exchanges with their targets posing as colleagues, competitors, or service providers and investing time to gain the victim’s trust before convincing them to provide their credentials. They also utilize watering hole attacks in which the attacker compromises a website that they hypothesize their target will visit and use it to infect their systems with malware. 58% of attacks on financial institutions rely on company employees to gain access and 90% are unwitting pawns as they are victims of social engineering or watering hole attacks (Carter, 2017).
DDOS attacks from Internet of Things (IoT) devices happen when multiple compromised systems are used to target a single system. Most international banks have contracts with at least one major DDOS mitigation service as one in three financial institutions experience a minimum of one DDOS attack per month. With new technology being established such as cameras, medical devices, smart TVs and more, these devices can be transformed into bots if they lack security and are therefore unprotected. Additionally, there has been a proliferation of dozens new IoT botnets, some having the capability of generating hundreds of gigabytes per second (gb/s) of traffic. However, even with DDOS prevention software, attackers have moved to using IoT botnets to generate overwhelming floods of traffic or, conduct “low and slow” attacks that avoid detection by DDOS software.
Ransomware is a form of malicious software that blocks access to a computer system until a sum of money or, “ransom” is paid. It has also become one of the most popular forms of attack and according to a survey conducted by SANS, 55% of banks have been subject to ransomware attacks.
Automation provides unsophisticated hackers a means to infect vulnerable systems. While off-the-shelf malware kits are readily available to be purchased by these criminals, they still facilitate the launch of more advanced attacks. This automated tool finds vulnerable systems and uses a cheap, out-of-date exploit to infect the system. Even with a small number of institutions being found vulnerable, the low-cost execution still makes the crime highly profitable. Payloads (the malware) are also using more automation tools with polymorphic and metamorphic features that make the malware harder to detect and block. Additionally, the hackers will often utilize self-propagation where the malware spreads itself throughout the computer/network without any human intervention or assistance.
Smaller, unsecured banks lead to larger banks and hackers frequently utilize a strategy in which they infect smaller financial institutions so that they can then send legitimate-looking requests to larger banks with the potential result for large payouts received by the attackers.
Hybrid attacks take place when hackers combine multiple methods of attack to yield higher success rates. DDOS attacks are most commonly being paired with breaches, multiple other DDOS methods, and ransomware. Particularly, when DDOS attacks are combined with breaches, the technical personnel are often too distracted with mitigating the DDOS attacks that the hackers breach the network to steal/manipulate data, implant malware, or commit fraud.
Blockchain offers some innovative solutions for these vulnerable institutions. Blockchain is a series of blocks that records data in hash functions with a timestamp and link to the previous block. The blocks are anonymously stored with other stakeholders within a network and cannot be overwritten.
All of this transactional data is also verified with every relevant stakeholder, which in turn makes data manipulation impractical. Additionally, this distributed and decentralized nature of the network that verifies the integrity of the transactions and associated account balances make a successful attack mathematically difficult.
For financial institutions, blockchain has three inherent qualities that are particularly appealing and relevant: the required authorization, identity format and lack of repudiation. There is an authorization or, permission-driven version of blockchain that is well suited to the needs of banks. They specify who among the network can view, modify and validate a transaction, which automatically creates a layer of protection for customer data and privacy. In regard to the identity format, blockchain provides an extra protection to personal information. This is done by recording it in a 256-key encrypted secure hash algorithm (SHA) format that is virtually impossible to hack.
This digital identity that the bank creates for its customer is required to be further validated through consensus as well. There is also a quality that entails no repudiation as the ledger is inherently immutable. This is because before a transaction can be hashed and put on the chain, it must first be validated by the network. Additionally, once a transaction is approved, it cannot be denied.
Blockchain ensures confidentiality, availability and integrity. Confidentiality is ensured through the permission-driven version of blockchain that restricts access to a trusted circle. The SHA algorithm also provides identity and privacy. With availability, blockchain eliminates intermediaries, which reduces lead time to near zero. The ledger is also replicated across several nodes, which means it is always working. Finally, integrity is ensured as every transaction in the ledger is visible. It is also impossible to fake or even deny a transaction after it has been completed.





