-
Bank of America Corp. is fighting fraud by teaching customers at the exact moment they are fooled.
May 5 -
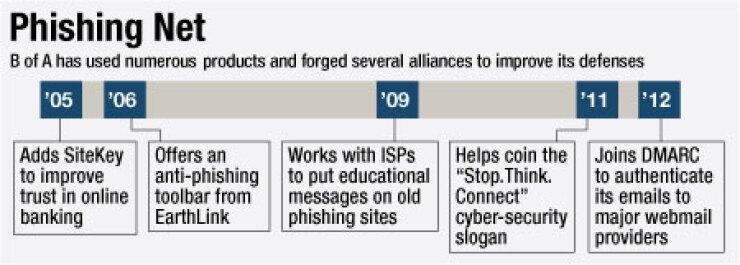
By joining a new anti-phishing coalition this week, Bank of America is maintaining a leadership position it's held for several years in the battle against cyberthieves who target online and mobile banking users. But this is one small step and the battle is by no means over.
"They're not perfect, they're siloed, but Bank of America takes security really seriously and they're not shy about experimenting with new ways to improve business," says Avivah Litan, vice president and distinguished analyst at Gartner. "They were the first to market with a lot of new security features." It was the first major bank to use images to heighten online banking security, with a feature called
The second-largest U.S. bank has good reason to get out in front of phishing, which is arguably the largest pathway to online banking fraud. (In the typical phishing attack, a cybercriminal sends an email that looks like it's from a consumer's bank and fools the consumer into divulging personal information, say, by asking the person to confirm account information. That information, of course, can then be used to conduct all manner of online banking and mobile banking fraud.) Bank of America has the largest number of online and mobile bankers in the U.S. and is therefore the biggest bank target. "They always jump on board first, I think the other banks will follow," Litan says.
The new coalition announced this week, called Domain-based Message Authentication, Reporting and Conformance (DMARC), aims to create a standard mechanism for verifying that an email has been sent from the entity it purports to be from. The group, whose 15 corporate members also include Google, Yahoo and Microsoft, will build on existing email authentication standards PKIM and SPF to put forward a standard for authenticating email domains. Under the new standard, participating email providers such as Google would check that email addresses are registered with the proper digital signature for the sender's domain (e.g. @paypal.com).
There are a couple of catches. First, standards like these, including PKIM and SPF, have existed for years and past efforts to coalesce them into one have been futile. The DMARC standard could take three to five years to become official and broadly adopted.
Second, even if the standard becomes formally accepted, to be effective, all email providers would have to sign on. "Even if only 50% of them sign on, that cuts it down so that the bad guys can still get to the non-users," Litan says. Every small company that has its own email addresses would have to sign up and make changes to its email systems. "That doesn't mean you shouldn't attack the problem, you want to put as many locks on the door as possible, even if there are ways around them," she says.
Brett McDowell, chairman of DMARC and a senior manager of customer security initiatives at PayPal says he expects adoption of DMARC to be widespread.
"In 2012 we will see many companies adopt DMARC policy records to monitor their email and authenticate traffic," McDowell says, adding that companies that have evaluated DKIM and SPF before, but have not invested in it, will see a clear value proposition with DMARC.
DMARC leverages DKIM and SPF standards, McDowell says, as more than 80% of email that is not dropped immediately as spam has been authenticated by email providers with the two existing standards.
Security vendors will also make DMARC standards part of their products and services, McDowell says. Such vendor services will further drive adoption in 2013, he says.
"This will be the end of domain spoofing, because you cannot deliver a message from a domain protected by the DMARC rejection policy," McDowell says.
Overall, the DMARC initiative would be an incremental improvement, Litan says. "It shows that phishing is getting worse," she says. "I've been getting more calls about phishing over the past few weeks than I have for months. It's not going away. To me, this is evidence companies are deluged with phishing attacks and they want to get serious about the standards."





