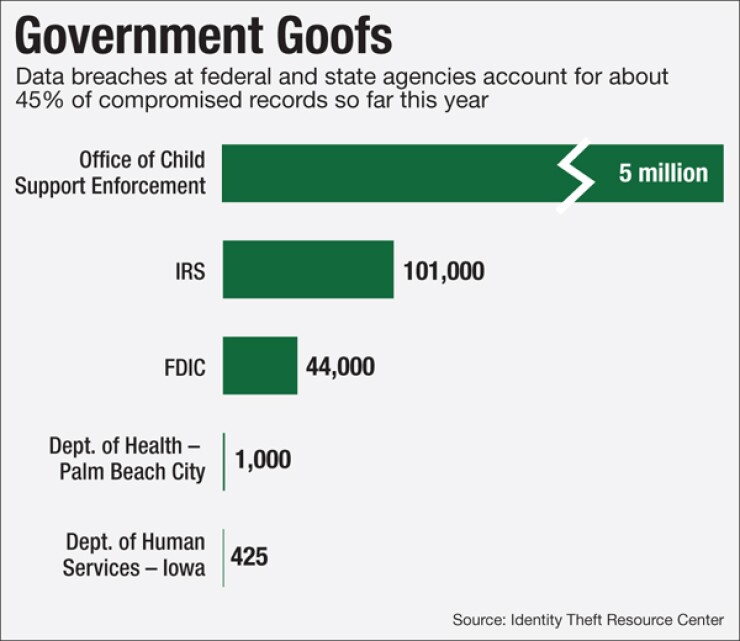
The FDIC's recent data breach of 44,000 records is a case study, mostly in how to handle a security incident well. It also highlights additional security controls all financial institutions should have in place.
On Friday, Feb. 26, an FDIC employee was packing up; it was her last day at the agency. She downloaded some personal files, such as family photos and her resume, from her work computer onto a USB drive to take home. At the same time, the FDIC later discovered, she inadvertently downloaded 44,000 customer records, including personally identifiable information, onto the portable device. The following Monday, the FDIC's data loss protection software detected the compromise of records and alerted security staff. The FDIC contacted the ex-employee immediately and asked her to return the drive; the agency had it back by March 1.
The agency also had her sign an affidavit stating she did not in any way use or share the information, which contained names, addresses and loan numbers of customers affected by bank closings. The FDIC is required to maintain such records to ensure the accounts are closed properly and any outstanding assets can be returned to their rightful owner. The employee had business reasons to access the customer records because she worked in examinations. She just wasn't supposed to walk out the door with them.
-
A former Federal Deposit Insurance Corp. employee took off with data on some 44,000 customers of closed banks when she left the agency in late February, according to an agency memo uncovered by The Washington Post.
April 11 -
Hackers did not steal banking or payments data from Experian, but they might as well have. Breaches like the one sustained at the company call into question the entire system of identification that banks rely on to open accounts and conduct other everyday business.
October 2 -
A data breach-related court case involving Wyndham hotels and new Defense Department rules governing contractors provide banks some dos and don'ts in bringing vendors' security practices into line.
August 31
The FDIC reported the incident to Congress as "an abundance of caution," said FDIC spokeswoman Julianne Breitbeil. "We caught it as quickly as we could."
Security incidents like this one are not uncommon in financial services. A little over a year ago, Morgan Stanley revealed that the financial adviser Galen Marsh copied names, addresses, account numbers, investment information and other data for about 730,000 accounts onto his home computer. While he was improperly accessing the client information, Marsh was in talks about landing a new job with two Morgan Stanley competitors.
What the FDIC Got Right
The FDIC did many things right in this case. First, it had data loss protection software that detected the data download.
"Having the data loss protection in place is a point in the plus column," said Julie Conroy, research director at Aite Group.
The FDIC recovered the data right away and ensured that it hadn't been misused. It reported the breach to Congress and explained publicly what happened. On the other hand, during the course of the weekend of the compromise, the customer data could have been sold on the black market or used for fraud. So an even faster response would have been useful.
To prevent future data breaches, the FDIC is banning the use of removable media such as thumb drives.
"The majority of employees don't have access any longer and we're phasing out the rest," Breitbeil said. "There have been business reasons why some have had access, including examinations."
Robert Capps, vice president of business development at NuData Security, a provider of software that monitors human behavior for signs of security infringements, applauded this step.
"There are legitimate reasons to move files around a company on portable media, because sometimes email or file shares is not the right play," he said. "But you have to take precautions on that data to ensure that it's transferred to media that's encrypted."
Conroy said she was surprised the agency didn't already have such an anti-USB policy.
"That is definitely a best practice," she said. "At a number of banks I talk to, if there are computers that have access to this kind of sensitive customer data, for instance in contact centers, the USB ports on those computers are physically sealed off."
Further Steps
Government agencies and banks should also have policies and systems in place to prevent the commingling of sensitive customer data with personal and work files, Conroy said.
"Some of my clients [which are mostly large banks] are not allowed to have any customer data resident on their work laptop," she said. "It's all held on a shared central server environment. When you take an airplane flight, you don't have access to the data."
There's more the FDIC and banks could do to prevent breaches of this type, observers say.
"I think the FDIC needs to catch up with their security controls. We can't have the FDIC leaking this amount of sensitive data," said Gord Boyce, CEO of FinalCode, a provider of file protection software. "Even though they likely have regulations that say they need to hold on to it, they need to secure it as well."
One type of security software many large banks are investing in is analytics that sift through the many alerts generated by data loss protection software and other security and fraud monitoring systems, Conroy said.
"As I talk to folks across the ecosystem, right now one of the biggest challenges is figuring how to accurately triage and prioritize those alerts and figure out which ones you shouldn't be spending time with," she said. "Many large organizations are looking at technologies they can use to help provide context to those alerts to make sure they get worked quickly."
Software can provide context around each alert to help separate the true red flags from the low or medium-level concerns.
SAS, for instance, offers software that analyzes traffic and interactions that typically flow between points in an internal network. When a traffic pattern between two nodes dramatically increases, for instance, an alert will be sent, especially if one of the nodes contains sensitive customer records. IBM and FICO sell similar cybersecurity risk analytics products.
Such software isn't cheap, "but I'm seeing more institutions move in that direction because the threat environment is not going to abate," Conroy said. "We have to have something that can help us better interpret all the alerts that are being generated."
Another option is digital rights management software, which restricts who can do what with files inside and outside a company's network. Vendors of DRM software include Covertix, Fasoo, Microsoft, Seclore and FinalCode.
Such software could see where sensitive data is going, notice when it just got downloaded to a USB thumb drive or a Dropbox folder and delete it, said Boyce.
It would have given the FDIC the ability to trace the customer data and do something as soon as the files left the building, he said. "In this case, the employee was cooperative but if the employee wasn't cooperative, you'd want to have the ability to delete that information even after it's left your organization."
Digital rights management has been a tough sell in the past, partly because it can be expensive, difficult to implement and unappealing to users.
"You're adding to workflow, and whenever you add to users' workflow they tend not to adopt it," Boyce acknowledged. Newer versions are easier to use, he said.
No security solution is perfect. Sealing off USB drives means people could potentially save files to Dropbox or iCloud. Security risk analytics software might not flag the behavior of users with legitimate access to data. Digital rights management is limited in that it doesn't prevent people from printing or taking pictures of files. But taken together, these and other security devices can form a net that makes inadvertent data breaches unlikely.
Editor at Large Penny Crosman welcomes feedback at





