A recent audit of the National Credit Union Administration found the agency struggled to keep its own house in order when handling information technology equipment.
A report from the regulator’s Office of the Inspector General concluded NCUA did not adequately monitor, account or dispose of its IT materials. The two objectives of the audit were to assess the NCUA's IT equipment inventory policies, procedures and practices, while also determining if the agency adequately monitors the lifecycle of its IT equipment from start to finish. The audit's scope ranged from Jan. 1, 2014, through June 30, 2017.
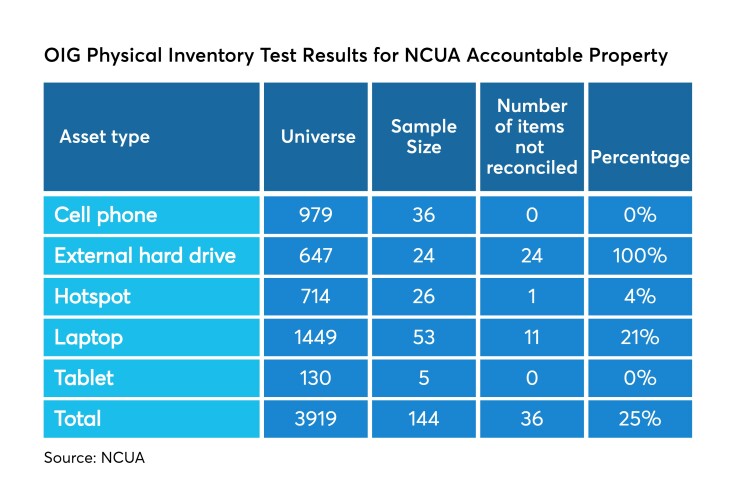
According to the report, the NCUA’s inventory records failed to account for 25% of the agency’s own equipment. With IT specifically, the OIG determined that NCUA held roughly 5,500 items at the conclusion of the audit’s period, though inventory records failed to match 31% of the actual equipment on hand.
The study comes less than a year after NCUA board member (and then-chairman) Mark McWatters was
The results of the OIG study have garnered a mixed back of responses.

Mike Lord, president and CEO of State Employees’ Credit Union, said the findings raise questions “about the new process that will be put in place regarding data that will be provided to NCUA by credit unions and what controls [the regulator] may have to safeguard, and what controls they will have in place for [personally identifiable information] so that member data is protected.”
Industry trade groups cautioned against making broad generalizations based on one report.
“NCUA is beginning continuous supervision programs where credit unions are giving them more data, so we would expect as part of any new initiative, NCUA would have to adequately demonstrate how they are safeguarding this information,” said Carrie Hunt, EVP of governmental affairs at the National Association of Federally-Insured Credit Unions.
The Credit Union National Association and the National Association of State Credit Union Supervisors declined to comment.
Cybersecurity risks
Among other findings in the report, the OIG determined NCUA spent roughly $440,000 on unnecessary equipment as a result of incorrect staffing projections prior to a government-wide hiring freeze and a subsequent reorganization of the agency in 2017 that lowered staff levels. While neither event was predictable, the OIG wrote, "We believe the $440,000 spent on what turned out to be excess IT equipment could have been funds put to better use.”
The agency was also said to have failed to properly dispose of IT equipment as promptly as possible, including 300 laptops that were identified as “exhausted or excess” in 2009 but not disposed of until 2018.

Failure to properly dispose of IT equipment in a timely manner can pose cybersecurity risks for institutions. John Grim, senior manager of investigative response at Verizon, noted that proper methods include overwriting devices with binary code or physical destruction of the device, among other techniques.
But Grim noted that getting rid of a device can be easier said than done, with factors such as the type of machine, its size and its hardware all playing a role in how the item is disposed of. Devices containing an optical disc are easiest to destroy, he noted, but technology with larger storage capacity often takes longer to decommission.
Regardless of disposal method, Grim recommended that all laptops be full-disc encrypted.
“It’s very likely or possible [that] if they’re not encrypted, there’s more of an urgency to make sure that those unencrypted devices are properly disposed of,” he said.
The OIG report did not note any problems with encryption.
In an email to Credit Union Journal, an NCUA spokesperson argued that much of the information in the report is outdated and the agency had already begun correcting many of the errors laid out in the report before the OIG issued its findings.
NCUA Executive Director Mark Treichel also penned a letter responding to the report, outlining several changes taking place in order to correct some of the practices the OIG outlined.
“Beginning March 31, 2020, management will annually survey the IT equipment, including a physical inventory of accountable property and identification of excess or exhausted IT equipment,” wrote Treichel. “We will sell, transfer or donate equipment according to the parameters established.”
The agency also plans to add a responsibility statement by the end of the third quarter to the paperwork it issues employees when they receive equipment. Along with that, management will be expected to update staff performance plans to define roles under the new accountability instructions that contribute to the effort of properly managing IT equipment.





