It's a perplexing problem for those developing and instituting Payment Card Industry data security standards: Even as threats rise, the number of organizations that fully comply continues to drop.
This is a trend that predates the COVID-19 pandemic. Fewer organizations were demonstrating the ability to "keep a minimum baseline of security controls in place" in 2019, according to the
From an assessment of PCI-DSS compliance data compiled from 68,992 controls across 60 countries and 334 PCI compliance validation reports, Verizon found that just less than 28% of organizations achieved full compliance during validation in 2019. It was an 8.8% drop from the previous year, when only 36.7% demonstrated full compliance.
One key problem area: Only 47% of organizations in the Americas had changed vendor defaults on security systems or had a system in place to monitor them, according to the report.
With retail, financial and hospitality industries showing the fewest organizations in full compliance, Verizon researchers noted that "poor performance on compliance assessments isn't a spontaneous act, but rather the outcome of a sequence of activities and events based on strategic planning, or a lack thereof."
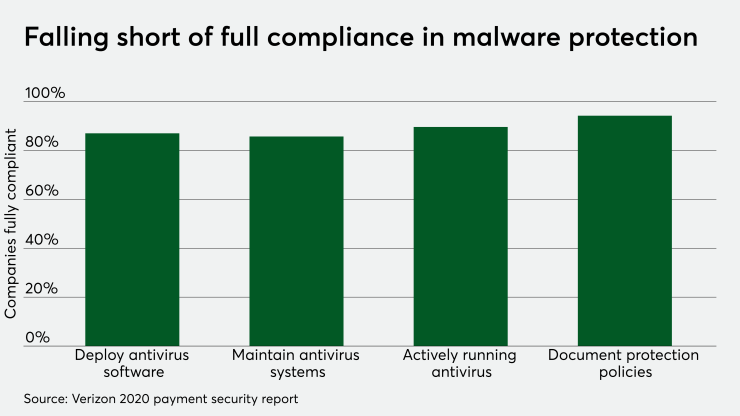
Not enough companies are paying attention to every aspect of data security as established through PCI requirements.
"After all these years of talking about breaches, we are still talking about breaches," said David Mattei, senior analyst with Aite Group. "We still haven't found a way to stop them, though we are faster at detecting them and quicker at containing them, but we are still plagued with them."
Last year, organizations handling payment card data were least compliant with PCI-DSS 3.2.1 in three key areas — testing of security systems and processes, developing and maintaining secure systems, and overall security management.
The requirement of testing of security systems and processes has ranked at the top of those with the least compliance in the last three Verizon annual reports. In contrast, the requirement of restricting access to a security system has ranked as one in which organizations have been most compliant in that time frame.
Even requirements that continued to show high compliance rates registered slight decreases in full compliance. The requirement for thwarting malicious software was one example, with full compliance falling 3.1% from the previous year. Yet, various aspects of the requirement had high compliance marks, such as documenting protection policies at 94% compliance.
"The challenge for some organizations is that they do not invest enough ‘security capital’ into their organizations to have security as part of the everyday culture," said Troy Leach, senior vice president and engagement officer for the PCI Security Council. "That requires investment in security to analyze the risks often, to regularly encourage training for all staff that resonates with their role and budget against the increasing automation of malware bot and other threats."
Companies often fall behind in their security measures because security is a moving target, Leach added.
"PCI DSS is intended to be evolutionary with the changing payment landscape and associated threats," he said. "If an organization’s security remains static for many years, you’d expect to see a decline since the threat actors have significantly improved."
Many PCI DSS requirements emphasize the need to regularly monitor for changes to risk and encourage the adoption of technology such as P2P encryption and tokenization to minimize the attack surface where payment data can be compromised, Leach noted.
The Verizon report noted that many organizations lack long-term strategies and still have trouble convincing senior business leaders of what it takes to keep data secure. It outlines the top strategic data security management traps that cause organizations to fail in implementations of a strong culture for security.
Verizon cited inadequate leadership, failing to secure strategic support, lack of resourcing capabilities and falling short on sound strategic design as key problem areas. Other troubling aspects included deficient strategy in execution of security measures, low capability and lack of continued improvement in the system and communication and culture restraints.
"Payment security must be a 24/7 priority that is maintained by a culture of security," Leach said. "Education and training of security professionals also needs to be a priority."
The problem for future security chiefs within organizations is that the job description continues to expand to the point where those in a top security position face mounting pressure, the study reported.
A chief security officer has to assess and implement security technologies and standards within the organization, as well as understand the threat landscape and manage the system to protect the business, the report said. The position also calls for creating overall strategies to innovate and trigger transitional change within an organization, while acting as an advisor who can educate and influence company activities.
And one of the best things a security officer can do for a company is take a serious look at cloud-based security systems, Aite's Mattei said.
"Businesses have been wringing their hands about moving to the public cloud, but the report shows 70% of breaches were of on-premise systems, while 24% were of cloud systems," Mattei said. "And of those cloud breaches, a good percentage can be attributed directly to incorrectly configured setups. This good should give businesses a good data point that a well-configured public cloud deployment can and is as safe, if not safer, than an on-premise deployment."
Verizon reported that 99% of security incidents in retail were financially motivated, with payment data and personal credentials "continuing to be prized." However, web applications — rather than POS devices — are now the main cause of retail breaches.
In financial and insurance breaches, 30% also were caused through web application attacks, primarily driven by external actors using stolen credentials to gain access to sensitive data stored in the cloud.
Credential theft and social attacks, such as phishing and business e-mail compromises, caused more than 67% of breaches across all industries, the report added. In 37% of credential theft breaches, criminals used stolen or weak credentials, while 25% involved phishing tactics, and human error accounted for 22%.
The report focused on 2019 payment security data points, but Verizon sees the current COVID-19 pandemic as a continuing threat to security.
“Unfortunately we see many businesses lacking the resources and commitment from senior business leaders to support long-term data security and compliance initiatives. This is unacceptable,” Sampath Sowmyanarayan, president of global enterprise for Verizon Business, said in a press release.
“The recent coronavirus pandemic has driven consumers away from the traditional use of cash to contactless methods of payment with payment cards as well as mobile devices," Sowmyanarayan added. "This has generated more electronic payment data and consumers trust businesses to safeguard their information. Payment security has to be seen as an on-going business priority by all companies that handle any payment data, they have a fundamental responsibility to their customers, suppliers and consumers.”





