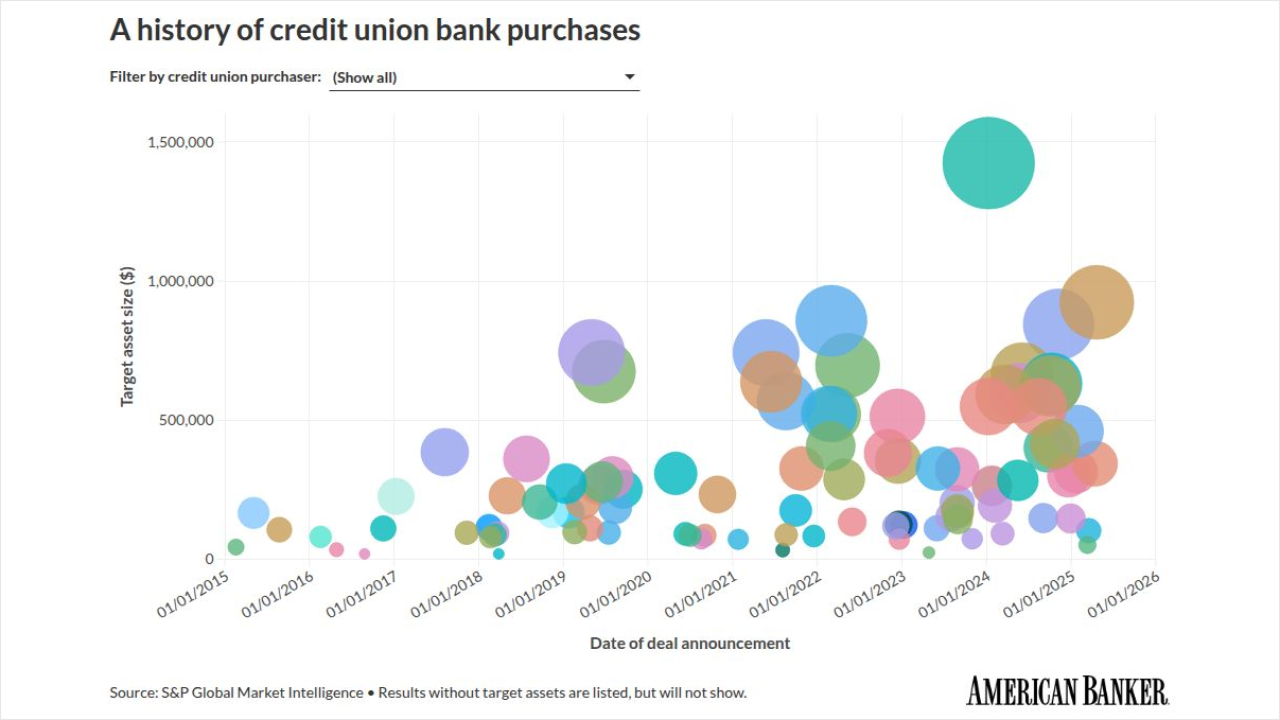
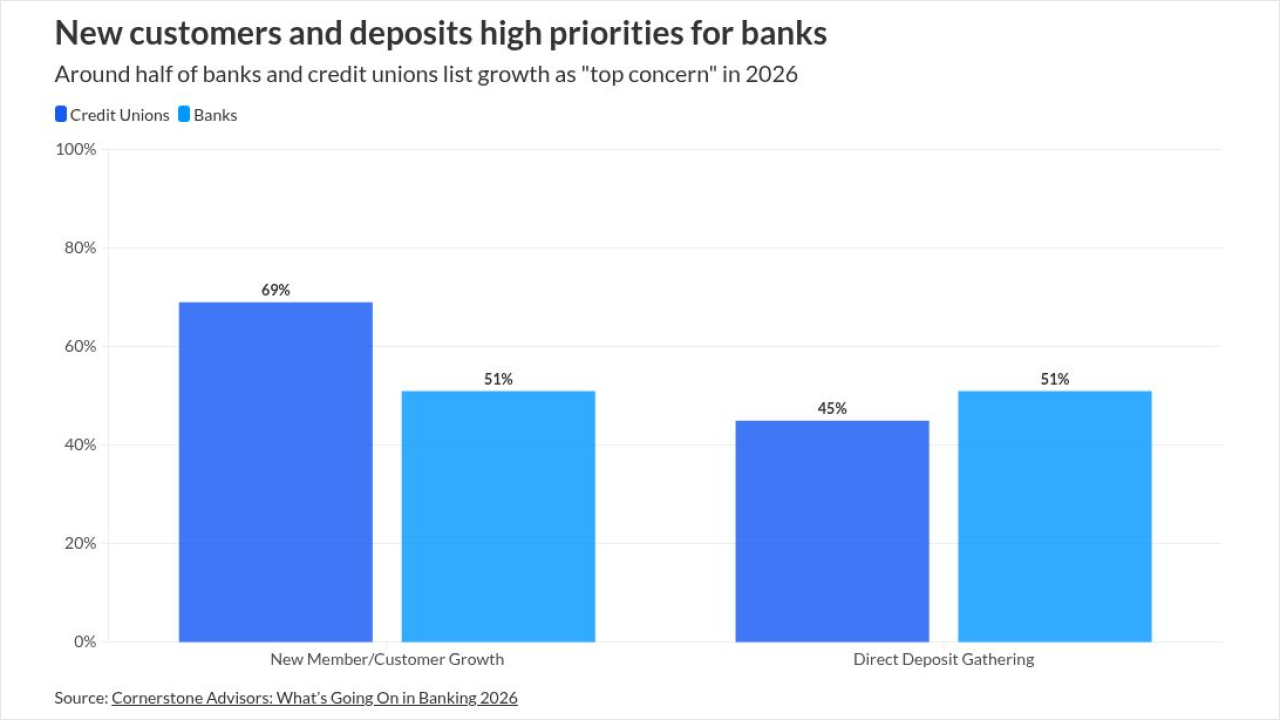
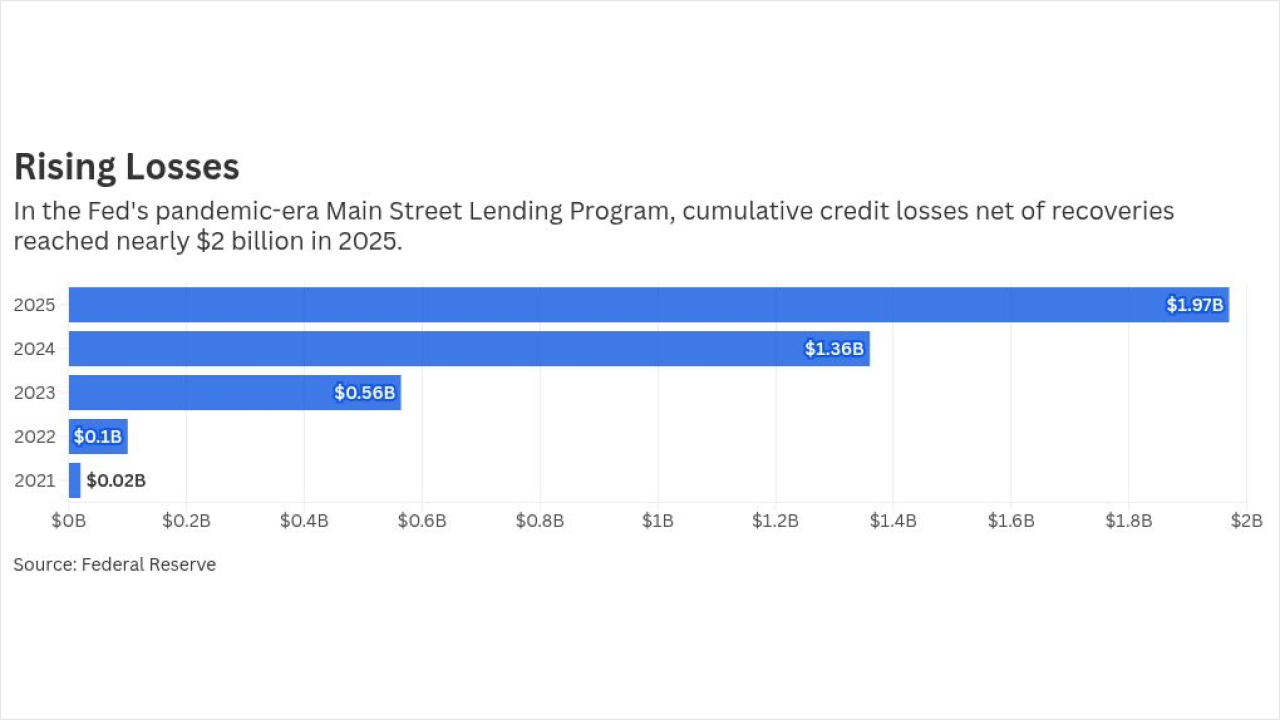
-
Big Blue is trying to combine the products of several security-tech companies it has bought in recent years into a fraud detection system that compliance-minded banks want to buy. The challenges facing the vendor and its clients overlap considerably.
March 20 -
To contend with a major security threat outside banks' control malware that online or mobile banking customers allow on their computers clientless detection products look at incoming transactions for signs of foul play.
July 8
If banks are serious about thwarting fraud or keeping it from spreading, then they need to do a better job of sharing information between departments and with rival banks and nonbank partners, industry practitioners say.
As it stands, a department responsible for tracking suspicious deposits and withdrawals often might not share its data with fraud analysts who are tasked with monitoring fraudulent debit and credit card purchases and other transactions. By not working more closely together, they could be missing out on an opportunity to spot fraudulent behavior or, with the help of law enforcement, bring down a criminal ring, experts say.
Similarly, if banks and third-party partners were more willing to share their stories of the fraud and security incidents they've been victim to, such as a check-kiting scheme or a denial-of-service attack, they could put the right defenses in place to keep intruders out of their databases and applications.
"Banks only have so much line of sight," says John O'Neill, a senior vice president at Bank of America. "We can only see so much of the data we have. If we use that as our only data source, we're never going to catch the large fraud rings that are stealing our customers' account information."
O'Neill believes that telecom companies and e-commerce giants like Google, Yahoo, and Amazon need to share fraud and security data with their bank partners. These companies need to recognize that they share the same customers and face the same cybercriminals, he says. "Keeping to yourselves is only creating more of an issue," he says.
Some comparing of notes on fraud and security does take place in the financial services industry. For instance, the Financial Services-Information Sharing and Analysis Center in Washington, D.C., gathers some information about fraud and security incidents from its members, anonymizes it, and sends it back out in the form of reports. The National Cyber-Forensics and Training Alliance in Pittsburgh holds meetings in which subject matter experts from different industries share threat information.
Some banks have set also up their own, private, closed-door peer networks of colleagues at different banks who know and trust each other and share information on a less-formal basis.
"As stewards of the industry, our job is to share as much information as we can through our partners," says Aaron Glover, senior analyst at SunTrust Banks in Atlanta. SunTrust, for example, has built a relationship with the Internal Revenue Service in Atlanta in which the bank sometimes calls to verify Treasury checks. The bank recently asked the IRS about one $300,000 check, which turned out to be linked to an IRS investigation, so SunTrust put the check on hold.
But despite such one-off successes, there's a strong need for protocols for information sharing about money laundering, corporate security and fraud, Glover says.
One group that is trying to tie together fraud data from many corners is NCFTA, which is building a giant database of threat information, collecting data from financial, government, and healthcare sources.
"We're sharing threat information, we're sharing information about compromised accounts, and it's enough to stop transactions," says Maria Vello, the president and CEO of the NCFTA.
The group has relationships with cohorts in Canada and the U.K. that have helped thwart the activity of international fraud rings, she says.
In one example, as Shylock malware was hitting the U.K., the U.K.'s Center for Information Sharing obtained the malware code and shared it with the NCFTA, along with the intelligence that it was targeting the U.K., Italy and the U.S. (Shylock is a family of malware that tricks customers into providing bank login or account details to hackers when they think they're interacting with their bank.) "We pushed that information out to our partners, and they were able to put up their defenses," Vello says. Bank members could adjust their malware detection software and behavioral analytics software to look for signs of Shylock-generated activity, and help their customers from falling victim to the malware.
But cooperation can be hard, largely because banks are often unwilling to share information. A few years ago, the NCFTA and the financial industry's equivalent, the FS-ISAC, tried to forge an alliance to freely share threat information. However, the FS-ISAC's bank members rejected the plan, saying they did not want their bank customers' information shared with other industries.
Bank members praise the FS-ISAC for the work it does in gathering security incident information from banks and reporting it back. The group has also begun automating its process, to send threat information that can be directly read and acted upon by banks' security systems. It will issue a new update to this system in June.
But insiders also say banks don't always send the right people to the group's meetings and calls those who truly know what is going on. "When I'm sitting on an FS-ISAC call, people are saying, 'no, we don't have any fraud,'" says one member. "Who are you and how much do you make, because I want to hire you," the member adds, sarcastically.
"Your fraud losses are a function of how bright your flashlight is and if you're shining it in the murky depths," Glover says. "A lot of people say they don't have fraud, that's either because they don't have a functional flashlight or they're not shining it in the right direction. If you're shining that flashlight, you'll be overwhelmed at what you'll find."
Legal boundaries are one disincentive to share information.
Some are trying to get sections 314(a) and 314(b) of the USA Patriot Act, which are meant to be a safe harbor for banks to share information without fear of prosecution, rewritten to be more specific and give banks' lawyers' assurance that the data sharing is OK.
"There's a lot of misunderstanding and legal teams tend to be about risk aversion," Glover says. "Sometimes you have to be a little cavalier to fight fraud."
Without clarity, lawyers at different banks "are going to read that same statute in 15 different ways," another bank security manager says. "Until they get down to cleaning up the 314(a) and (b) to what it was really meant to be and not what lawyers believe it was meant to be, it's going to make it difficult to get that information shared."