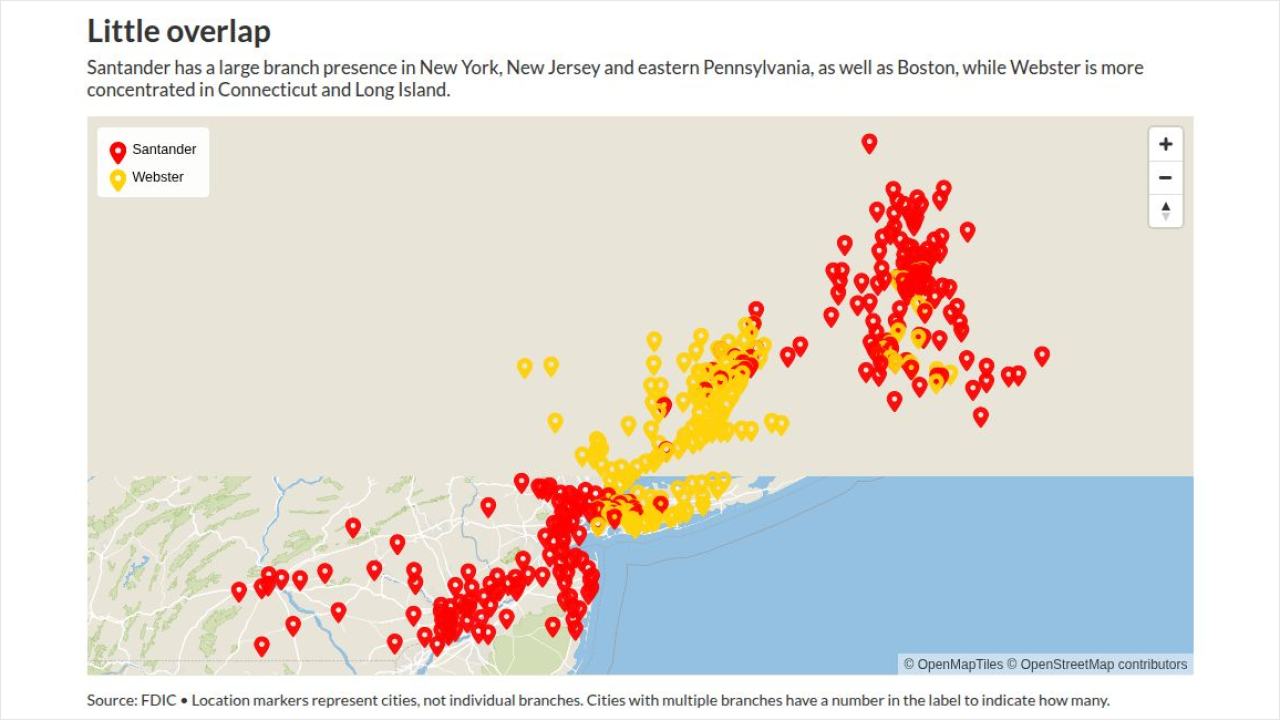
As a growing number of state and federal regulators come out with their own rules about how companies should respond to cybersecurity incidents, bankers have asked that these new regulations align with each other so that, when their teams scramble to respond, they can spend more time securing their systems and less time worrying about compliance.
Bankers are not alone in making this ask. Leaders in cybersecurity and the software industry, which serve as key vendors to banks, also want harmonization for their own reasons.
In
Bagley said that each of the many new and proposed rules on cyber incident reporting are "well-intended," but take place simultaneously and with different stakeholders, meaning the potential downside is "burdensome, distracting and costly compliance obligations without additional security gains." The antidote, he said, is "muscular harmonization efforts."
During the hearing last week, Heather Hogsett, a senior leader of the Bank Policy Institute's technology policy division,
BPI supported a bipartisan law
BPI framed the law at the time as an opportunity for CISA to establish one rule to harmonize the
Several federal agencies have recently stepped up requirements on banks to notify regulators and the public when they fall victim to cybersecurity incidents.
Hogsett specifically called out a proposed rule from the Securities and Exchange Commission, which is expected to be finalized
Hogsett said during her testimony that this rule would "undermine" the work of CISA and other regulators, in part because those notifications are public rather than merely shared with and between government agencies.
Compliance with these rules can also be costly for banks, which spend 40% of their cybersecurity budgets on compliance,
Other groups have also expressed support for harmonizing cyber incident rules, including a trade group that represents the interests of business software vendors, the Software Alliance. In its 2023 Global Cyber Agenda, the Software Alliance (formerly the Business Software Alliance, or BSA) highlighted "harmonizing laws and policies within and between governments" as one of its five priorities.
As a federal advisory commission considered
"Certainly, the notion of CISA driving a single, harmonized rule-making process across the federal government is attractive," said Eric Wenger, senior director for technology policy at Cisco, "but there is a flaw with this argument because CISA has no authority over independent federal agencies. Among federal agencies, CISA has a unique cybersecurity-oriented mandate. It can singularly focus on targeted information sharing that will balance the cost of generating reports on victims with the benefit to the security ecosystem from timely reporting requirements. CISA can develop rules for incident reporting that are laser focused on improving cybersecurity and are not reliant on the reporting standards established and followed by other federal regulatory agencies."
The risk in focusing on harmonization is that in the name of achieving a single, unified reporting standard, CISA might then be required to accept the terms demanded by other agencies, which may have a different focus than CISA's focus on improving the nation's cybersecurity.
After a federal advisory committee
"One of the great strengths of CISA has been its focus on security, and it's been able to advance goals that everybody shares," Lilley said. "Once you get into regulation, politics tends to get a bit more pronounced."