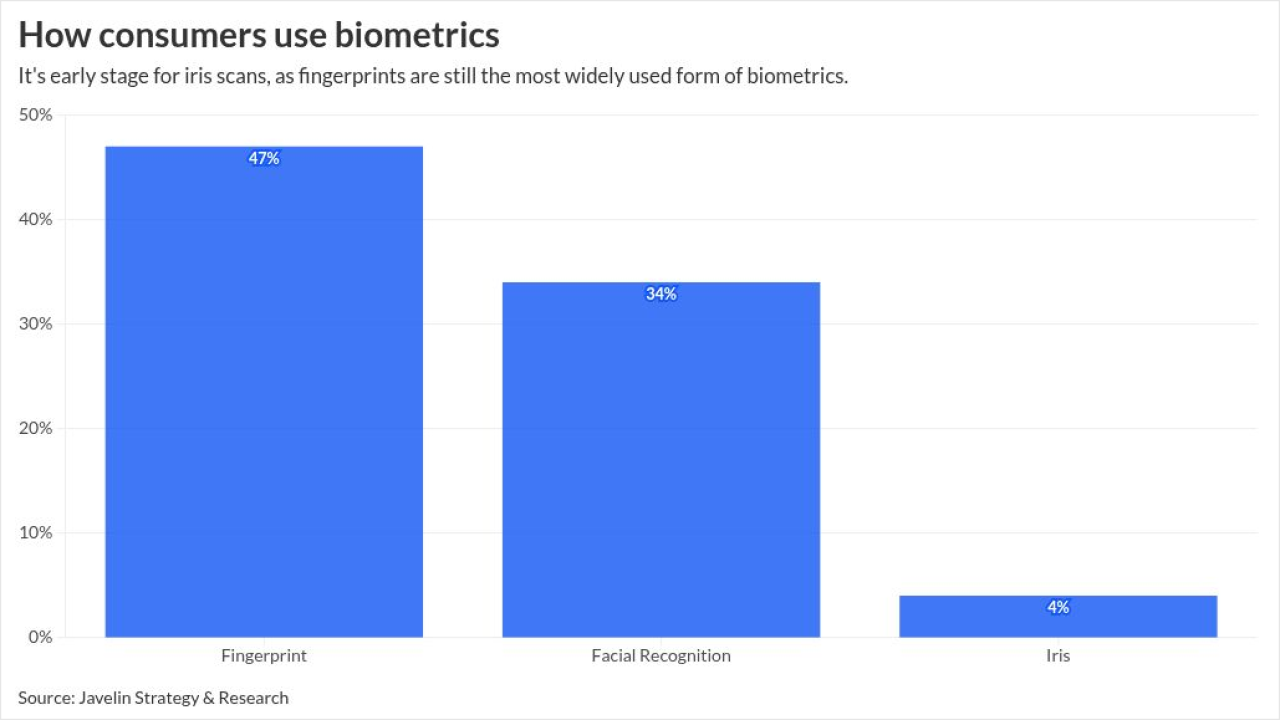
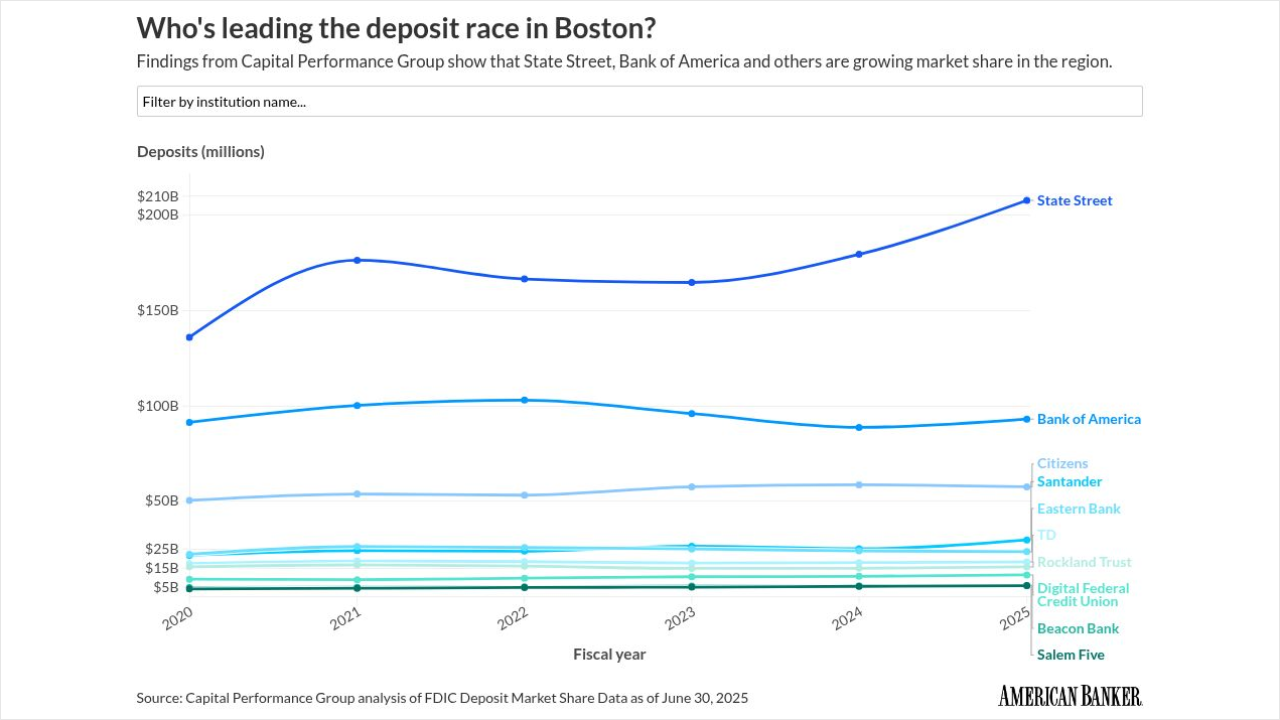
-
Banks have been under siege for about a year. An in-depth look at the main types of attacks, the "bad actors" and their motivations, and what banks are doing about it.
October 7 -
DDoS attacks, ACH fraud, and account information theft are problems, but is it hyperbolic to talk about war cyber war?
October 7
Having interviewed 100 bank executives, merchant fraud executives, and security vendors about cybersecurity over the past year, Julie Conroy, research director at Aite Group, is struck by three things.
One is that the threats against banks keep multiplying, as a fan of the original Star Trek series might say, like
A second is the speed at which "bad guys" continue to innovate and adjust their cyberattacks on banks. When she spoke to many of the same bankers a year ago, most hadn't suffered any corporate account takeover losses in two years. "They had deployed robust, layered security, and were feeling pretty good," she says. Fast forward 12 months, and several of the banks had taken four or five losses totaling $1 million or more. By the end of 2013, more than $500 million worth of corporate account takeovers will have taken place globally this year, Aite estimates. The total is expected to reach $800 million by 2016.
"The bad guys adjusted rapidly," Conroy notes. "The fraudsters had recognized the fact that dual controls had been deployed and used social engineering to get around those dual controls." Business clients are the most attractive because "you can get the most bang for your buck," Conroy says.
"They're without question quite sophisticated," she says of the perpetrators. "In some countries you've got the best and brightest doing this stuff because there's a lot of money to be made." The bad guys don't have to make a business case to innovate, she points out. Banks have to make a business case and then go through a very lengthy cycle between the time of recognizing the need for new technology and getting it deployed.
Banks have invested a modest 5-10% more on security in the past year than in earlier years, Conroy estimates.
"Fraud prevention and security is a cost center, so you don't always get the ability to make huge incremental increases," she observes.
What are they investing in? Some are completely rethinking authentication and working on device analytics. When an anomaly is detected, that can trigger out of band authentication or knowledge-based authentication (aka challenge questions). Many are gravitating toward IVR-generated phone calls to confirm transactions, she says. Merchants are more hesitant to make such calls, as they are sensitive to intruding on a transaction and possibly driving a customer away.
Banks are also investing in secure browsing technology, Conroy says. "The challenge is in many cases, there's a client that needs to be downloaded onto the end user's computer," she notes. A handful of banks have made secure browsers mandatory. But most have not; overall adoption rates hover around 14-15% for wholesale banking.
The third conclusion Conroy drew from her research was that financial institutions and merchants could learn a lot from each other about security, if they would only talk a bit more. "Typically these are two groups that are in opposing positions in the market, and they don't always collaborate," she says. But often they're up against a similar foe with similar tactics.
A platform from Ethica facilitates the sharing of chargeback information between merchants and issuers. Normally it takes 38 days for a merchant to receive notice of a chargeback, Conroy points out. Using Ethica the information is sent within a day. In 33% of cases, the merchant is able to stop shipment, which stops the merchant from taking a loss, she says.
Collaborative forums provide the opportunity to pool case information together, she says. If a crime ring hits a bank for $20,000, it will have trouble getting law enforcement interested in its case. But if the ring hit several other banks or merchants for similar amounts, the companies can put their examples together and go to law enforcement with a much stronger case.
Data breaches, a huge headache for banks four years ago, have become a less significant worry. Earlier this year, Verizon found a drop in large data breaches.
But they're still a concern, Conroy says. The Adobe breach last week affected 2.9 million customers.
"When those things happen, it affects everyone," Conroy says. "From the banks' point of view, it's their number that was compromised, and that number can be potentially used at the point of sale or online. So they have to make the decision, how likely are the bad guys to sell this data as a result of this compromise? Do we reissue the card or just put it in a higher watch category?"
The banks she spoke to worry about "back of wallet" risk when they reissue cards - the fear that consumers will have a negative association with that card and not use it for a while or as often, and in the meantime, they'll get used to using another card.