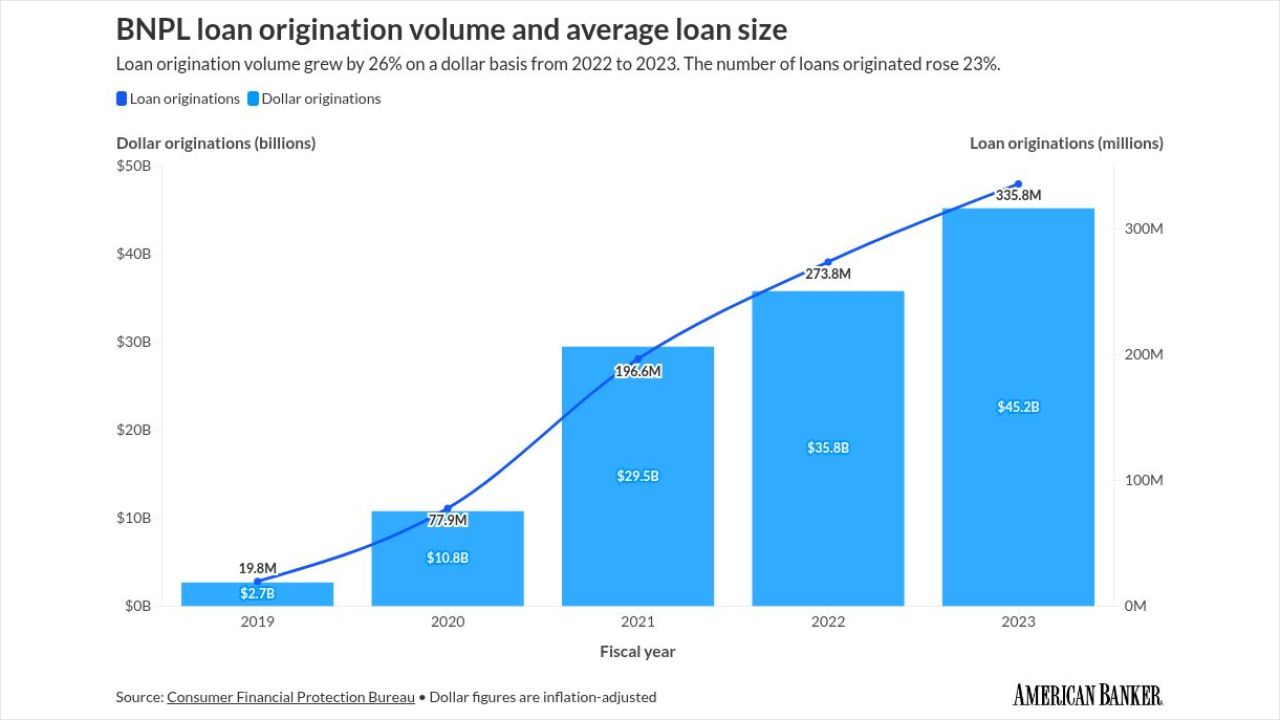
-
The Federal Reserve is making clear that the status quo, in which U.S. electronic payments take days to complete, is not going to hold, an industry analyst says.
September 8 -
The banks involved in Apple's mobile payment platform cite the enhanced security, intuitive user experience and brand name. Even if they sacrifice fees, they could make it up on volume.
September 10 -
Within the past 12 months, one large retailer after another has fallen victim to a massive data breach. But at least the pilfered data is getting harder for thieves to monetize.
September 9
In the classic New Yorker cartoon, one dog says to the other, "On the Internet, nobody knows
The payment systems used in the United States today were not designed with the built-in security to handle payments generated from the Internet. The New Yorker cartoon is from 1993, so this problem has been building for more than 20 years. If it is not quickly addressed, I fear that the confidence of the public in the bank payment system and therefore the banking system itself could be severely shaken.
With our legacy bank payment systems, the "keys" that move money, such as account numbers, are accessible at multiple points during the transaction life cycle. The "keys" are "in the clear" and accessible to many parties to a transaction. Security experts will tell you that in a secure Internet-based system, the security "keys" must be encrypted at all times and shared only as minimally necessary to complete a transaction. Otherwise, a system cannot be made secure.
The security of any network is only as good as its weakest node. By opening access to the legacy payment systems to the Internet, we added tens of millions of nodes to each legacy payment system and most of those nodes are not securely authenticated or truly secure.
When I was first told in the early 1990s that industry leaders believed we didn't need to build a new payment system for Internet-sourced transactions, that businesses could safely use legacy credit and debit card systems to sell goods and services on the Internet, I was shocked. Our bank has avoided these risks over the years, which from a safety and soundness perspective are incredibly high.
Although major fortunes were made along the way by those who embraced insecure payment methods and ignored the risks of an inherently insecure system for Internet payments, the criminal ecosystem is finally catching up and these risks are multiplying rapidly.
The Target breach, in which 110 million Americans lost critical personal and financial data, is just the largest problem caused by extending legacy payment networks built in the 1960s to Internet-originated payments.
The rapid rise of
In addition, for Internet-sourced payment transactions, a next-generation payment system should:
- Encrypt and secure all data, from end to end;
- Never leave data "in the clear"; and
- Ensure all users are "strongly authenticated" and "strongly enrolled."
What is "strong enrollment"? This requires one's identity to be proofed at the time of enrollment, "eyeball to eyeball," while checking and comparing with a government identity document that meets the
What is "strong authentication"? This combines a physical trait a biometric such as a voiceprint or fingerprint, captured during the strong-enrollment process with a personal possession, such as a cell phone. Note, however, "shared secrets" that can be stolen, intercepted and shared (like a mother's maiden name or where you went to elementary school) cannot be the basis for strong authentication.
It is less expensive by orders of magnitude to build a new next-generation payment system that can do these things than to retrofit one of the existing legacy payment systems.
To be clear, the legacy payment systems are highly secure for what they were designed to do. Wires and automated clearing house transfers, for example, were designed under the assumption that an authenticated and strongly enrolled bank employee generates a payment message that is sent to another bank. There, another bank employee, also highly authenticated and strongly enrolled, posts that payment to the bank's deposit ledger system. Credit and debit card systems likewise assumed "card present," in person transactions. I believe that Internet-sourced transactions should be banned from these systems unless they can meet the required level of security.
I know that a highly secure next generation payment system can be built using off-the-shelf, proven technology in less than a year. Do we still have a year left before our current systems hit the wall?
Stephen Lange Ranzini is the CEO of University Bancorp in Ann Arbor, Mich. He has been an active participant in industry technology standard-setting bodies such as