Malicious hackers tend to swarm around industries they perceive as vulnerable, and terminal makers are the latest to find themselves in the crosshairs.
Years ago, payment processors seemed to be a favorite target — Heartland Payment Systems, Global Payments, RBS WorldPay and more
"The hackers are not going after retailers as much, but they are going after the POS vendors," said Stephen Boyer, chief technology officer, for BitSight Technologies, which measures and rates companies' cyber security performance.
Most recent research from Cambridge, Mass.-based BitSight indicates that one in four data breaches involving payment card data have the POS terminal or network as the source of the compromise. It's an indication that criminals have switched their past focus on payment processors and retailers and are finding the companies that provide equipment to be easier targets.
In addition to payment card data, hackers inside a POS provider's network can find human resources and employee information, e-mail lists, website credentials, and details about other services the company may provide, Boyer said.
"This is really important for the industry to understand because the hacker is thinking all he has to do is go after a POS vendor and then get into their hundreds of thousands of endpoints," Boyer said. "Get the passwords for remote management and you get into a network to exploit not just one retailer, but maybe hundreds and thousands that the company services."
It's also why the retailer may get the immediate headlines when a breach occurs, but the source of the breach is increasingly becoming the POS provider, not an oversight on the retailer's part.
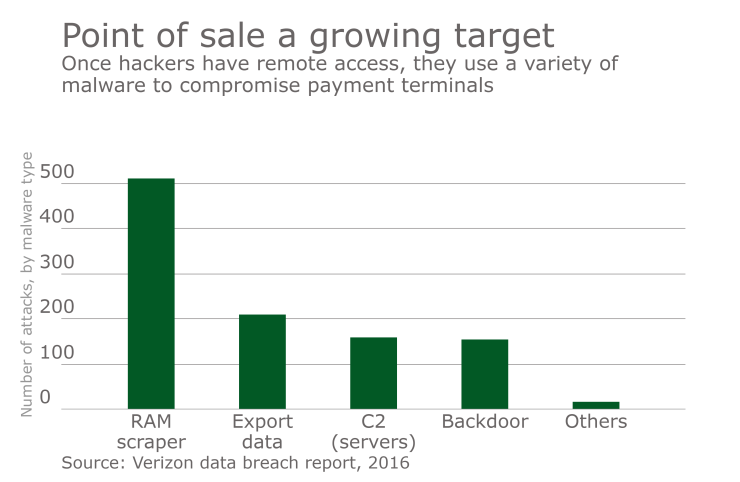
Verizon's 2016 data breach investigation report warned that the new trend of attacks against POS vendors was picking up steam, citing 97% of POS breaches featuring stolen credentials came about when a hacker used legitimate "partner" access to enter a network.
"This year continued the trend of the criminal sprees in our data being associated with attacks against POS vendors, followed by using their access into the customer database," Verizon said in its report. To combat that, Verizon encouraged merchants to make sure their POS vendor had a second access factor beyond a password; something like a hardware token or mobile app, as well as a system for monitoring login activity.
But the incidents continue.
Last week, the upscale Cleveland-based
It's worth noting that the Verifone incident, which Krebs covered, affected its internal network and did not affect its payments service network. The Verifone incident also illustrates what may become more common for POS vendors in quickly explaining to clients and media what happened.
Information security teams at Verifone "identified evidence of this very limited cyber intrusion into our corporate network in January of 2017," Verifone said. While saying it was in immediate contact with the card brands and its clients to explain the breach, Verifone also sought to minimize fears in saying there had been "no adverse effects or misuse of any data" resulting from this incident.
There are other incidents, such as three years ago when more than 200
With that sort of success, hackers have quickly placed attacks on payments supply chains, with the goal of obtaining remote management passwords and codes, at the top of their target list.
Indeed, hackers have been licking their chops over the prospect of getting into terminal vendors' inner sanctums for many years.
"In general, fraudsters will push and probe at the financial services value chain, looking for windows of opportunity," said Julie Conroy, research director and fraud expert with Boston-based Aite Group. "When they find an open window, they intensively attack it, knowing they have a limited time before that avenue of compromise is sealed."
The payments industry is all too familiar with the way fraudsters focus on a particular vertical whenever they believe they have found a weakness.
"The hotel and restaurant POS systems that were compromised in multiple events in 2015 and 2016 are a good example, often taking advantage of the fact that the user never reset the default password," Conroy added.
Possibly even more alarming, and further down the supply chain, Conroy said instances were confirmed last year in which mobile devices being shipped out of China had malware pre-loaded.
The bigger technology players are not immune. Late in 2016, Oracle's
"The retailers do as much as they can to lock down their own systems, but the people who do the service to these endpoints are getting compromised," BitSight's Boyer said. "And then the retailer is compromised as a result. It's a really hard problem."
No one had a magic formula in hand to predict and warn the payments industry a few years ago that the POS vendors would be the next in line of a hackers' pecking order that started with processors like Heartland and continued with major retailers like Target and Home Depot.
"The attackers move quickly from one weak spot to the next weak spot," Boyer said. "To be thinking years ago that you were probably the next target, that's a lot more foresight than a lot of these companies have."
Still, in many sectors of business, it is becoming common knowledge that the supply chain represents a huge security gap. For companies in that sector, having strong security becomes a competitive differentiator, Boyer said.
"People want to use those systems, and they have to think about functionality and security practices of those organizations," Boyer added.





