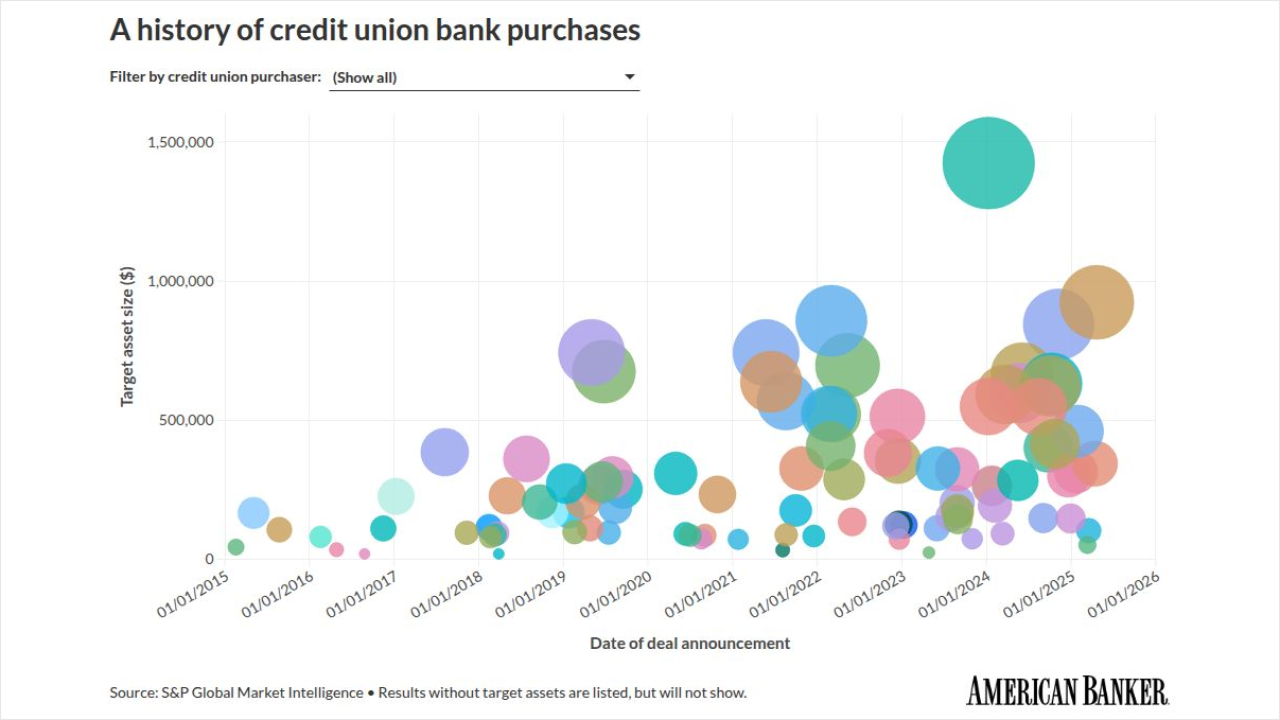
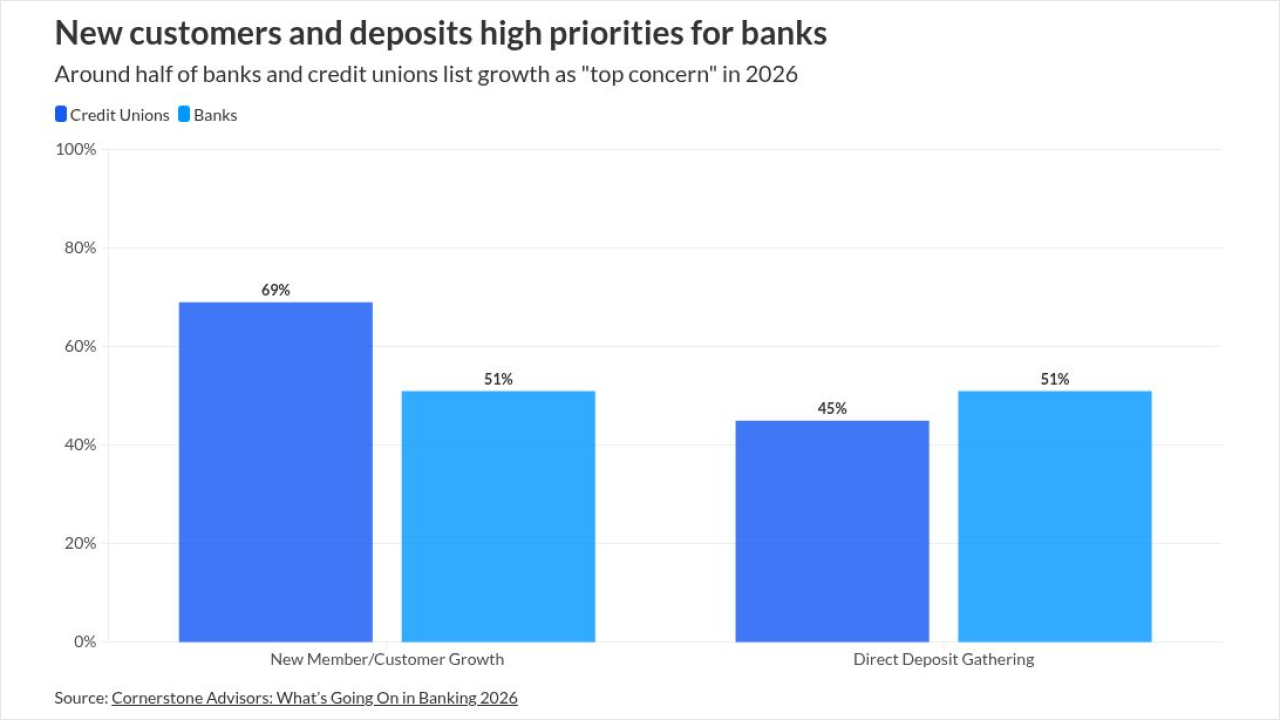
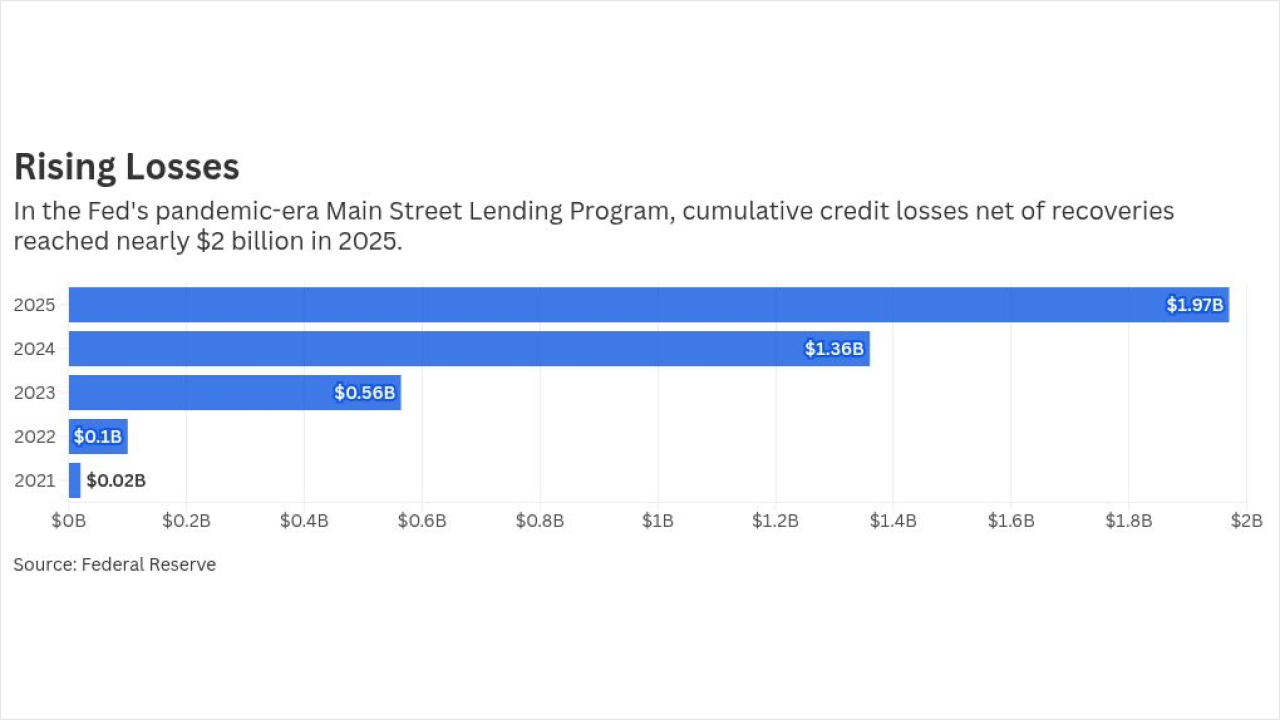
A new malicious spam campaign that has been targeting Internet users in the U.K. serves as an important example of how banking malware targets business as well as home users.
The emails of particular campaign,
When that does happen, an interesting twist shows that this campaign was built with a big target in mind.
The attachment to the email is a Word document in which malicious macros are embedded. When allowed to run, these download
This particular version of Trickbot doesn’t just install itself on the infected device, it also looks around the network to see if it can infect other devices. In particular, security blogger Brad Duncan
Domain controllers play a core role in any modern Windows-based computer network as a central server that determines who gets access to which machines. For malware, such machines are thus a prime target.
This kind of lateral movement is becoming increasingly common in malware; it is, for instance, how the WannaCry malware managed to do much damage within the U.K.’s National Health Service. In the case of banking Trojans, it serves as an important reminder that for a business, having a dedicated machine to do only online banking isn’t secure enough if malware can travel inside the network.