Cybersecurity professionals are having hard time keeping up with the vulnerabilities exposed on a daily basis in networks handling payments or personal data, according to new research from Bay Dynamics.
A closer look at the number of weak spots and how security teams go about addressing them demonstrates that professionals are dealing with such a high volume of threats that they struggle to prioritize which ones to fix.
Research firm Enterprise Management Associates surveyed more than 400 cybersecurity professionals for Bay Dynamics' first report on this topic. Bay Dynamics is a cyber risk analysis and prevention firm with offices in San Francisco and New York.
The report comes out just a few days after the WannaCry
The fact that the attackers found a gap in the operating system through a weak spot that had a patch issued for it months ago is a perfect example of the problems facing network security professionals.
With a backdrop of enterprises with more than 20,000 employees trying to manage more than 1.3 million network vulnerabilities every 30 days, 74% of respondents say they are overwhelmed by the volume of maintenance work needed.
On top of that, 79% say their patching approval process is "significantly manual," slowing down their ability to implement fixes.
Overall, 64% say that threat alerts are not addressed each day, which is not surprising considering 79% said they were overwhelmed by the volume of those alerts.
The threat of cyber attacks and an inability to defend against them is the same problem for large and small organizations, said Steven Grossman, vice president of strategy at Bay Dynamics.
The big companies have more manpower and tools, but also face more threats. Small companies have less exposure, but fewer experts available to handle them.
As for the manual patching process, Grossman said that means security professionals are struggling to balance their own needs with those of the people using the systems that need to be patched.
"If someone puts in an order for the IT guy to patch the system, he can't just take down an application that might be critical to a business system or, in the case of health care, critical to life safety," Grossman added. "There is a whole coordination process that has to go on to make sure the business keeps running when that patch happens."
The timing of the patching process depends on the "criticality" of the threat, Grossman said. When the danger is high, IT operations generally move quickly to patch a network in hours or days.
For low-priority fixes, the work could be postponed indefinitely, creating an opportunity for fraudsters to exploit a vulnerability that should have been closed off to them, Grossman added.
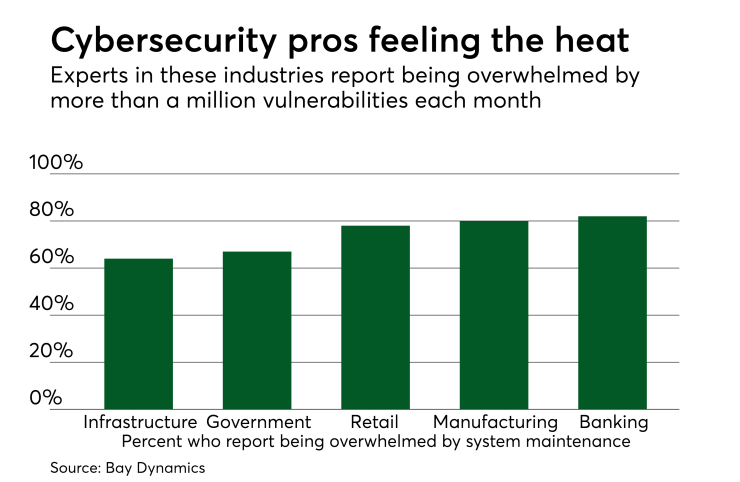
The stress of keeping up with security patches is apparent across industries, with 67% of respondents in government saying they were overwhelmed with network maintenance. In retail or wholesale settings, 78% said they had a hard time handling maintenance work assigned to them. The banking/financial industries ranked highest at 82% feeling overwhelmed.
Another stress factor is whether the threats are being effectively triaged. Just more than half of respondents said threat alerts are improperly prioritized by the systems in place and must be manually ranked.
Such an approach is "indicative of a less mature program" and drives more work to staff and delays the resolution of the truly high priority alerts, the report said.
"If a job gets a reputation for being high-pressure and low-reward, you will have trouble attracting people," Grossman said. One solution is for companies to automate as much of the analysis and patching process as possible to offset limited manpower, Grossman added.
"I don't think the bad guys are overwhelming us as much as we are overwhelming ourselves by not having the right processes in place to fix things," Grossman said.





