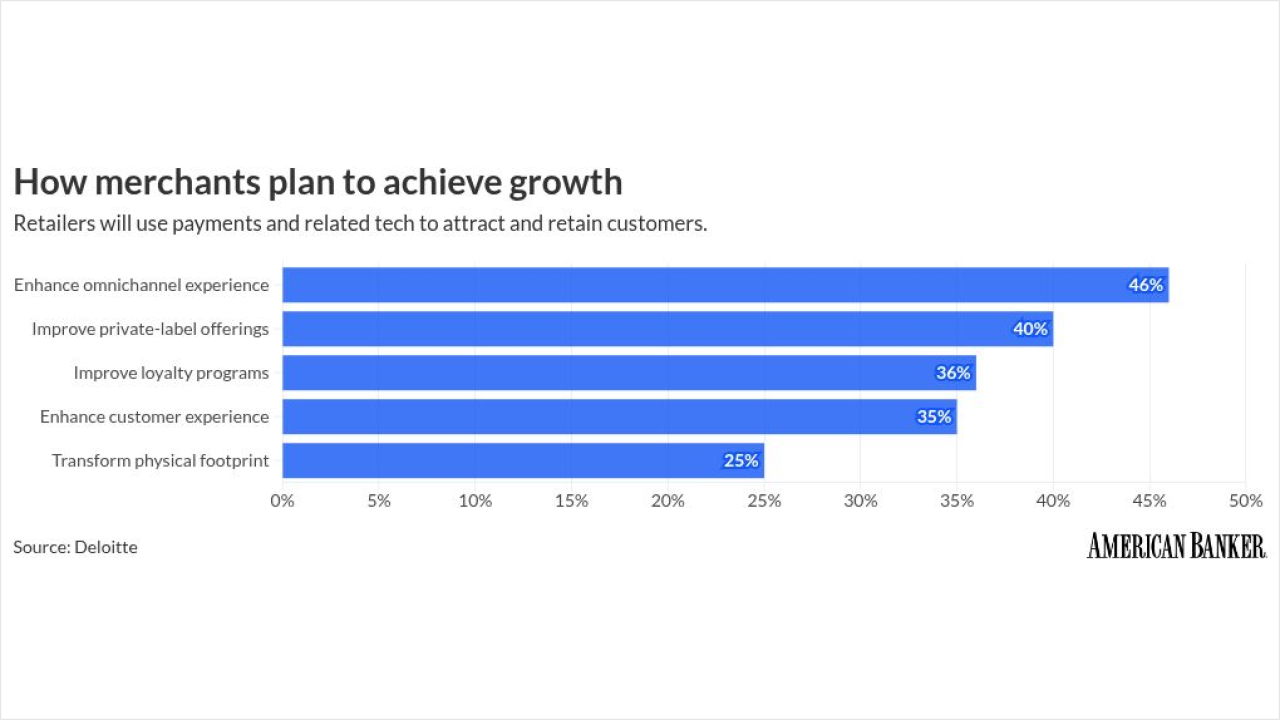
-
Gemalto NV, the largest maker of mobile- phone cards, said it's investigating a report that U.S. and U.K. spies allegedly hacked into its computer network to steal the keys used to encrypt conversations, messages and data traffic.
February 20 -
Decisions about when and how to implement EMV technology in credit and debit cards are difficult. Many banks have decided to slowly phase it in, despite the fact the delay will open them up to greater potential liability.
February 18 -
This week's White House Summit on cybersecurity at Stanford University comes at a pivotal time for payment and security professionals, who have an opportunity to cooperate to fight Internet crime.
February 12 -
Recent reports that the National Security Agency has been undermining encryption on the Internet have led to speculation about the security of online banking data.
September 12 -
House Republicans grilled the Consumer Financial Protection Bureau's acting deputy director Tuesday over how the agency gathers and protects consumer data.
July 9 -
A hack that exposes information on cellphones' SIM cards could potentially endanger customers' bank information.
July 23
The apparent hack of Gemalto by U.S. and U.K. spies casts doubt over several security measures vital to the payments industry as it embraces chip cards and adopts digital payments.
Gemalto, a Dutch company that manufactures SIM cards and EMV chips, is
The incident sends a message to the banking and payments industries that "all of this stuff can be hacked," said Julie Conroy, research director and fraud expert with Aite Group in Boston.
Keys like those allegedly stolen from Gemalto are used in "point to point encryption," the practice of encrypting customer data from the point of interaction (for example, when a card is swiped) until it reaches a secure environment. A form of key management is used in tokenization, which replaces sensitive information with tokens when the data is "at rest." The payments industry is developing
The loss of an encryption key would harm any company trying to protect data.
In payments, providers supply a public (or asymmetric) encryption key or a shared (or symmetric) key. Those keys encrypt the personal account number at the terminal or PIN pad to protect data as it moves through a network. Encryption keys are generally stored in a hardware security module or through cloud-based software vaults.
It appears from the report that hackers compromised the entire Gemalto network, accessing numerous data encryption keys that go beyond telecommunications, said Greg Coogan, president and CEO of West Bay Partners, an information technology consulting company.
Payment companies would have some protections in the case of a Gemalto hack, according to Coogan. The incident "doesn't really [directly] address tokenization and EMV and the types of standards expected out of the people who provide those services," he said. For example, Visa and MasterCard security protocols make it clear that a merchant or financial institution "would never get e-mail access to tokens," Coogan said, referring to the report's suggestion that hackers stole vital information from e-mails or shipments of SIM cards from Amsterdam-based Gemalto.
The Gemalto event likely won't trigger the same type of fear that resulted from the breach at RSA Security in 2011, Conroy said.
In early 2011, hackers broke into the
Major breaches at security specialists like RSA indicate that nothing is truly safe "if there is a sufficient amount of monetary, corporate espionage or state secret incentive" to pursue it, Conroy said.
"A key difference in the Gemalto case, depending on one's point of view, is that theoretically these were the good guys trying to access information," she said. "But people view privacy differently in different countries."
Coogan agreed, but wondered if data in the hands of "guys in the white hats" can reach others with different intentions.
"We are hoping they were doing this for a reason, in an attempt to keep us safe," Coogan said. "But that doesn't preclude [someone] from causing chaos with information about EMV chips or other data."
Constant network monitoring and multiple layers of security remain the most important defensive measures for any retailer or business protecting payment or other sensitive data, Conroy said.
Gemalto did not respond to direct inquiries. In a statement to media outlets, it noted that, according to the report, the company was not a lone target and the breach was part of an "attempt to try and cast the widest net possible to reach as many mobile phones as possible to monitor mobile communications without mobile network operators and users consent."
Gemalto said it cannot verify the findings at this time, though it was taking the report seriously. The company also reminded its clients that it has dealt with other breach attempts and is "especially vigilant against malicious hackers."