Wireless-network connections at brick-and-mortar stores are the latest focus of payment-security angst.
First, court documents released this past fall confirmed that insecure wireless local area network connections at two stores owned by TJX Cos. likely created the holes thieves used to access servers at the merchant’s headquarters. There they poached improperly stored card-transaction data from most of TJX’s 2,400 stores in the United States, Canada and United Kingdom.
Then, just in time for this year’s holiday shopping season, wireless-security services vendors demonstrated to the consumer media that many merchants around the world continue to use the same outdated wireless encryption that was TJX’s first failed line of defense.
The public flogging of brick-and-mortar stores for vulnerable wireless-network connections has renewed calls for tighter payment-system security and, of course, has continued the debate about which players in the payment chain should pay for that security.
Network-security wonks have known for years about “war driving,†the practice of would-be hackers cruising streets or casing parking lots armed with laptop computers or other devices that can detect vulnerable wireless signals. Payment card data and detailed customer information that enable card fraud or full-on identity theft are favorite prizes of such electronic burglars.
A segment on the 60 Minutes television show on Nov. 25 highlighted the practice to an American public already skittish about payment card security. Riding in a minivan with Kris Harms, a computer forensic investigator for Alexandria, Va.-based Mandiant Corp., correspondent Leslie Stahl viewed on Harms’ laptop computer a list of service set identifications, which are names of wireless-network access points, including “Best Buy†and “Staples.â€
Too Much Information
Besides clearly noting the owners of the networks, the list on the laptop screen also showed whether merchants they were passing were using wired-equivalent privacy (WEP) connections; the newer, more-secure, Wi-Fi-protected access (WPA) network encryption; or no encryption at all.
Mandiant is not the only security vendor taking advantage of retail-wireless encryption’s 15 minutes of fame.
In November, AirDefense Inc., an Atlanta-based company that provides security services and products for wireless networks, announced the results of its investigation of physical and wireless network security at 3,045 retail stores in the United States and Europe.
Armed with wireless laptops, investigators cruised around some of the world’s most-famous shopping areas in Atlanta, Boston, Chicago, Los Angeles, New York City, San Francisco, London and Paris.
During six weeks from September through mid-October, AirDefense investigators found that 85% of 2,500 wireless electronic devices used by stores, such as laptops and hand-held bar code scanners, were vulnerable to hackers. Twenty-five percent of wireless-access points used no encryption at all. Seventy-four percent of access points were encrypted, but 25% of those used the WEP protocol that the updated Payment Card Industry Data Security Standard declared in September 2006 to be inadequate protection for payment card data.
Richard Rushing, AirDefense chief security officer, says investigators detected wireless networks of many stores using the same types of wireless-network routers shipped to residential Internet customers, often using default passwords that hackers more easily could identify.
“We wondered why we were seeing this in a shopping mall,†Rushing says. “You peek behind the desk and there it is: the same one I’ve got at home.â€
Paris showed the fewest number of poorly named networks, with only 3% of wireless signals from 394 stores monitored in that city showing store names or obvious pseudonyms. In Los Angeles, 35% of 262 stores monitored with wireless network connections used names that easily identified the merchant, the highest percentage among the cities AirDefense studied.
AirDefense found a higher percentage of stores in London and Paris using the recommended WPA and WPA2 encryption protocols. In Boston, by contrast, 32% of retail wireless-access points monitored were not encrypted at all.
Rushing says many larger retailers that have installed WPA encryption at some payment-network access points keep old WEP connections active because they have one or two older point-of-sale devices that are not compatible with WPA. And hackers can break WEP encryption within five minutes, he says.
“If you’re keeping WEP turned on because you have one or two old devices, the risk is too high,†Rushing advises retailers. “Just go buy the two [WPA-compatible point-of-sale] devices, or 10 devices or 100.â€
Not doing so was the mistake TJX executives made, according to e-mail messages released recently as evidence in litigation. Three New England bankers associations and seven financial institutions spent last year in U.S. District Court in Boston seeking to recover their costs associated with having to reissue cards crooks may have accessed in the TJX breach.
By the time most of them settled with TJX last month, TJX had turned over to plaintiffs’ attorneys more than 2.5 million pages of documents, including a Nov. 23, 2005, message to colleagues from Paul Butka, TJX chief information officer.
He wrote: “We can be PCI-compliant without the planned FY ‘07 upgrade to WPA technology for encryption because most of our stores do not have WPA capability without some changes. I think we have an opportunity to defer some spending from FY ‘07’s budget by removing the money from the WPA upgrade, but I would want us all to agree that the risks are small or negligible.â€
Epic Breach
The rest is history, specifically the largest payment card breach in history in which crooks accessed from TJX’s server information on an estimated 100 million credit and debit card accounts and some Social Security numbers, driver’s license data and checking account information of customers who had returned merchandise without receipts.
TJX and its acquirer in the U.S. and Canada, Fifth Third Bank Processing Solutions Inc., as well as Visa Inc. and MasterCard Worldwide declined or did not respond to requests for interviews for this article. But the banks’ case in Massachusetts also made public years of internal discussions about TJX’s security status.
TJX stored Track 2 magnetic stripe data and complied with only three of the PCI security standard’s 12 categories, according to references in court to a forensic audit by Trustwave division SpiderLabs and a report issued in September by the Office of the Privacy Commissioner of Canada. Track 2 data include the full credit card number and its expiration date.
After thieves first hacked into the wireless network–TJX told Canadian investigators that may have occurred outside two Miami-area Marshall’s stores in July 2005–they tunneled their way to network servers at the TJX headquarters in Framingham, Mass. TJX owns Marshall’s. Hackers visited the network again in September and November 2005 and from time to time from mid-May 2006 to mid-January 2007.
Thieves gained administrative privileges to the network’s retail transaction-switch servers that store cardholder data for most TJX stores in the U.S., Canada and the United Kingdom. Then they used file-transfer protocol software to copy Track 2 data and transfer it to another machine via a high-speed Internet connection at TJX’s headquarters.
Dave Hogan, chief information officer of the National Retail Federation, agrees that TJX made a lot of mistakes, including storing Track 2 data. “Nobody should be storing that stuff,†he says.
But Hogan says it is not easy for retailers to change payment hardware and software every few years when thieves figure out how to breach it and security rules change accordingly. “WEP was acceptable [under PCI] in early 2005, so all these companies went out and installed WEP,†Hogan says.
WEP Out, WPA In
In September 2006, the updated PCI Data Security Standard declared WEP encryption inadequate on its own and WPA more secure, leaving many retailers with point-of-sale devices incompatible with WPA.
Bob Russo, general manager of the PCI Council, an educational body that also coordinates discussions about PCI among card networks, financial institutions, merchants and other stakeholders, says he sympathizes with retailers trying to comply with standards that change to keep ahead of adaptable data thieves. “You’ve got people who made investments in wireless four to five years ago when the only thing available was WEP,†he says. “It’s not a big investment to switch to WPA, but it’s a time commitment.â€
Russo says retailers and other experts have provided the council with considerable feedback about wireless security in recent months. He notes that wireless is “one of the areas that’s going to be addressed†when the council prepares an updated version of the PCI standards in the first quarter of this year.
Hogan appeared in the 60 Minutes segment reiterating the federation’s argument that Visa and MasterCard (through their merchant acquirers) should not require merchants to retain some card data in case of transaction disputes. And he complained that card networks now are levying fines of $25,000 per month for the PCI noncompliance of some merchants.
“I’m not too sure how vested the card companies are as far as securing customers’ data,†Hogan told Stahl. “If you do the math on it, this could be a windfall of $200 million annually for the credit card companies as far as a revenue stream.â€
Regardless of the fines card networks are starting to levy now, court documents show their repeated forgiveness in nudging TJX toward security compliance. In a Dec. 29, 2005, letter to Fifth Third, Joseph Majka, Visa vice president of fraud control, wrote that Visa would suspend fines until Dec. 31, 2008, “provided your merchant continues to diligently pursue remediation efforts. This suspension hinges upon Visa’s receipt of an update by June 30, 2006, confirming completion of stated milestones.â€
In June 2007 Visa fined Fifth Third $880,000 for the shortcomings of TJX. But TJX reportedly validated PCI compliance in mid-October, so Visa agreed to rescind $225,000 in fines not yet collected for Fifth Third’s previous failure to ensure TJX’s compliance by Sept. 30, 2007.
And Visa on Oct. 18 agreed to restore TJX to more-favorable volume-based interchange rates. Visa’s PCI compliance-acceleration program penalizes noncompliant merchants with higher interchange rates.
Who’s To Blame?
During the bankers’ federal suit, TJX tried to compel MasterCard to provide testimony and documents they said would further illustrate how much MasterCard knew about TJX’s security problems. The defense argued that MasterCard, not TJX, was therefore responsible for breach-related costs that three MasterCard issuing banks were seeking to recover.
Visa also agreed in November to rescind $500,000 of that $880,000 on Fifth Third for “egregious†TJX violations, which Visa explained in a news release would free up funds for an “alternative recovery†program for financial institutions.
U.S. issuers of more than 95% of Visa cards affected by the breach agreed in late December to the settlement. TJX will pay financial institutions up to $40.9 million for breach-related costs. In return, the issuers agreed not to sue or seek other forms of recovery from TJX. The settlement did not involve issuers of MasterCard or other card brands.
TJX’s agreement with Visa also includes a provision for the merchant to take its newfound PCI religion on the road. According to a TJX filing with the U.S. Securities and Exchange Commission, TJX will “serve on at least four occasions†during a two-year period “as a spokesperson in support of the goals of the Payment Card Industry Data Security Standard and the security of payment card information.â€
Perhaps the fear of card-network fines or of becoming the next big news story will lead more retailers to beef up their own wireless-network security. It surely should make them wary of loiterers bearing laptops and other signal-scanning devices.
TJX Breach Timeline
Sept. 1999
Institute of Electrical and Electronic Engineers ratifies wired-equivalent privacy (WEP) international standard 802.11 to encrypt information traveling through wireless local area network connections.
2000-2001
Researchers and criminals discover ways to crack WEP encryption.
2003
Wi-Fi Alliance declares new Wi-Fi-protected access (WPA) encryption more secure than WEP, requires WPA security for certification of Wi-Fi products.
2004
Institute of Electrical and Electronic Engineers ratifies WPA2 standard and declares WEP inferior to WPA and WPA2 encryption.
Dec. 2004
First Payment Card Industry Data Security Standard released. WEP still allowed to encrypt payment data on wireless local area networks.
July 2005
First undetected breach of TJX network begins through WEP connections at two Marshall’s stores.
Oct.-Dec. 2005
TJX planning WPA-conversion project, but IT executives decide to delay WPA implementation.
Dec. 2005
Visa tells Fifth Third Bank it will suspend fines for PCI violations by TJX until Dec. 31, 2008, provided TJX “continues to diligently pursue remediation efforts.â€
May 2006
Hacker uses wireless connection to place “sniffer†tool on TJX servers in Framingham, Mass., headquarters.
Sept. 2006
PCI 1.1 released, declares WEP inadequate on its own for wireless networks handling payment card data. WPA acceptable on its own for handling card data.
Dec.2006
TJX learns that suspicious software has been detected on a portion of its computer system.
Jan. 2007
TJX hires division of Trustwave to conduct forensic audit of breached network. Banks file suit against TJX in federal district court in Massachusetts.
June 2007
Visa fines Fifth Third $880 million for TJX’s “egregious†security violations.
Nov. 2007
TJX agrees to fund up to $40.9 million pretax for alternative recovery payments to affected Visa issuers.
Dec. 2007
Most plaintiffs settle with TJX for some court costs. Issuers of more than 95% of affected Visa accounts accept TJX alternative recovery deal.
Sources: U.S. District Court District of Massachusetts, Office of the Privacy Commissioner of Canada, Office of Information and Privacy Commissioner of Alberta, Institute of Electrical and Electronic Engineers, PCI Security Standards Council.
(c) 2008 Cards&Payments and SourceMedia, Inc. All Rights Reserved.
http://www.cardforum.com http://www.sourcemedia.com
-
A bipartisan housing provision has emerged as a critical negotiating point for passage of an uncommonly bank-relevant defense authorization bill.
10h ago -
More than 400,000 consumers may be affected after Marquis Software Solutions suffered a breach traced to a bug in SonicWall software disclosed last year.
11h ago -
Midland States Bancorp has completed three major asset sales in the past 12 months, exiting national business lines and shifting focus to its core community banking franchise.
December 4 -
Employees throughout the company can use generative AI to query data from sales calls, email, invoices and a host of other information sources.
December 4 -
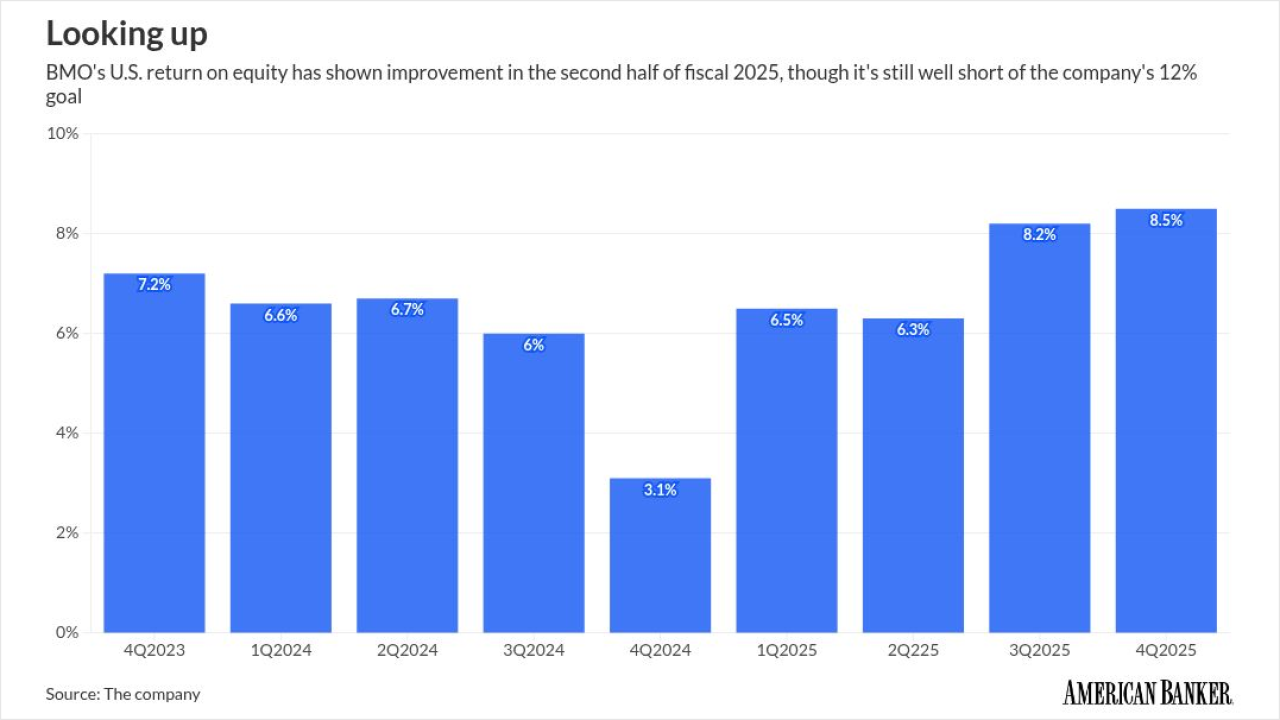
The Canadian bank is determined to grow its U.S. business organically, CEO Darryl White said Thursday. But with so much excess capital, analysts wondered about the bank's appetite for M&A.
December 4 -
The Canadian bank still has more work to do as it rolls out additional processes, technology and training. TD will also have to prove to regulators and the U.S. Department of Justice that its actions are sustainable.
December 4