Want unlimited access to top ideas and insights?
Consumers are becoming increasingly dependent on online services and tools as the world becomes more connected every day.
And as consumers, we expect these online services to do more for us and know more about us to make the experience more convenient. But that same information that makes these on-demand services useful is the same data that makes these services a target for hackers, especially as we continue to depend on a username and password to protect that data.
The latest
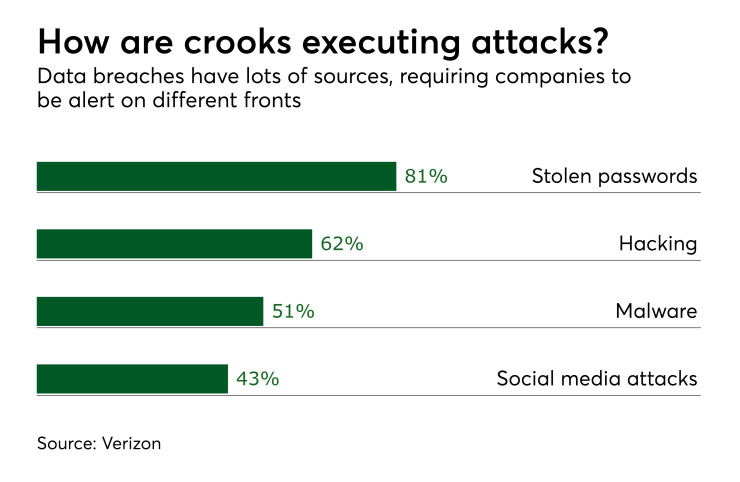
But common authentication solutions such as one-time passcodes or more complex passwords are not enough, and add friction and potential frustration for the user.
The solution? Mobile identity authentication. Mobile ID authentication can reliably and securely identify a mobile phone user through a greatly simplified user experience, reducing friction for the user without compromising security. Mobile ID authentication relies on a number of technologies that leverage both hardware and software techniques to securely store user credentials and reliably authenticate a user and that user’s mobile device.
More technically speaking, there are several ways to secure user credentials in mobile devices, the secure element (SE), trusted execution environment (TEE), and host card emulation (HCE). Each has advantages and disadvantages.
SE. Mobile ID credentials that are stored in an SE are protected using the same techniques that protect credentials on a physical chip card.
The advantages: provides tamper-resistance (against hardware and software attacks); uses cryptography; can provide lifecycle management of card applications through secure channels; and has compliance and certification programs to ensure interoperability and conformance to specifications.
The disadvantages: has limited memory; requires trusted, secured systems for lifecycle management; and requires business relationships to be established for access to the storage space and lifecycle management.
TEE. Credentials stored in the TEE are isolated from the rest of the operating system and applications to protect from threats potentially present in the system. TEE implementations can also leverage techniques such as encryption, tokenization, and code obfuscation to further strengthen the protections provided by the core TEE architecture.
The advantages: uses mobile device memory secured by a dedicated cryptographic processor; can store cryptographic keys in the SE or other hardware-based secured system; has defined specifications for a trusted user interface and secured storage; and has certifications to standardize implementations.
The disadvantages: usually requires business relationships to access the restricted trusted application execution environment and requires trusted, secure systems for lifecycle management.
HCE. Unlike the SE and TEE, HCE is not a security mechanism. Instead, it allows near field communications (NFC) commands to be routed to an application running in the smartphone operating system rather than being routed directly to an SE. The benefit of this approach is it allows credentials to be stored in several different ways, for example, via a cloud service, or in conventional memory on the mobile device. It is recommended that any HCE-based mobile ID application leverage additional techniques, for example, using an SE or TEE to enhance security, and additional techniques, implementing additional security mechanism such as encryption, tokenization, code obfuscation, or white box cryptography, and designing back office systems to detect fraud.
The advantages: requires no special access control (credential is stored in device’s main memory); is supported by Android operating systems, with similar approaches available for Windows and Blackberry phones; allows for remote and rapid updates.
The disadvantages: does not provide security; exposes application keys to the operating system; provides less security for credentials are when stored in the phone’s main memory; and requires applications to have their own security mechanisms.
For mobile ID authentication to be widely deployed, it must be based on accepted standards. Standards development for mobile ID authentication is still in the early stages, and the industry needs to continue to develop robust, proven mechanisms. The following includes a few examples of standards that have been or are being developed that developers and implementers alike should consider in their mobile ID authentication strategies.
The FIDO Alliance, an industry organization, has developed an open, scalable, and interoperable set of standards for simpler, stronger authentication including use cases where the mobile device is used for passwordless or second-factor authentication.
The FIDO specifications aim to help organizations reduce their reliance on passwords, and instead rely on the use of strong cryptographic techniques to authenticate a device to online services. Secrets are stored only on that device and are never exposed to the cloud, so services using FIDO authentication are not vulnerable to scalable attacks like phishing.
There are two options for user experience with the FIDO specifications: passwordless and second-factor. The passwordless experience removes the need for a user to have to enter a password every time they log in, instead using an on-device authenticator, like a fingerprint sensor on a mobile device, to verify that the rightful user is trying to access a service. The second-factor experience allows online services to augment the security of their existing password infrastructure by adding the requirement for a strong second factor, a device that is certified for security and interoperability by the FIDO Alliance, to user login. In this scenario, a user logs in with a username and password as before. The service can then prompt the user to present the second factor device at any time.
W3C Web Crypto API. The W3C Web Crypto API offers authentication mechanisms over common API interfaces to the underlying cryptographic key storage. This approach is applicable to a variety of use cases, such as multifactor authentication managed within a mobile application; protected exchange of documents by wrapping with public keys and unwrapping using private keys; cloud storage; document signing; data integrity protection; and secure messaging.
Web Crypto API defines low level interfaces for interaction with cryptographic key materials, which are exposed through an interface that provides common access functions and is managed or exposed by user agents. This API creates an agnostic layer to the applications that is compatible with multiple underlying key storage implementations from different cryptographic vendor solutions. Web Crypto API offers a common set of interfaces to rich web applications that can be used to access a variety of cryptographic operations, including key and hash generation and verification.
3D Secure. The EMVCo 3D Secure protocol enables bank card issuers to authenticate consumers directly for online transactions. This protocol is intended to prevent online transaction fraud and protect merchants from exposure to chargebacks. The protocol provides an additional layer of security and has different implementations depending on the specific payment network implementation.
The three domains are the acquirer domain (the merchant), the issuer domain (the card issuer), and the interoperability domain (the infrastructure, which includes software providers).
Client TLS Certificates. Client TLS Certificates provide two-way authentication between clients and servers. Within the handshake that establishes a secure session, the server may demand a certificate and proof of ownership from the client. Due to historical constraints on certificate delivery and extended trust relationships, this mechanism has until now largely been confined to enterprise networks, where it is frequently used for VPN or website authentication with smart cards or desktop certificates.
However, these constraints can now be avoided, due to the prevalence of smartphones and the availability of cloud services capable of easily deploying dedicated, affordable certification servers. Certificates can now be used as a highly secure and very convenient alternative to password authentication, especially when they are deployed in conjunction with biometric user authentication to the handset. Implementation of this mechanism requires a certification server.
A significant value proposition for mobile ID authentication comes from a powerful combination of the convenience provided to users together with the enhanced data available from smart devices. To date, the various use cases for mobile ID authentication have used a wide variety of means today to secure credentials. The mobile and computing industries recognize the potential, but also recognize the security and costs risks if each application chooses a unique method for mobile ID authentication.
There are both established and emerging standards for securing cryptographic keys and biometric templates on devices, as well as processing the authentication between a mobile smart device and the relying party service provider. Using standards and industry recommended best practices would benefit all stakeholders – providing a more consistent and convenient user experience and improving security overall.





