One of the many dangerous things about breaches is the amount of time it takes for companies and end users to know their data is out in the open.
From the moment a breach happens, hackers have ample time to broker the stolen names, payment card details and other identifying information on the dark web — leaving customers and employees open to the impacts of identity theft.
Huddle House, a chain of fast food and casual restaurants, recently suffered a breach at its point of sale systems.
Cybercriminals leveraged the chain's assistance tools to gain remote access — and deployed malware into the point of sale systems of some Huddle House corporate and franchisee locations.
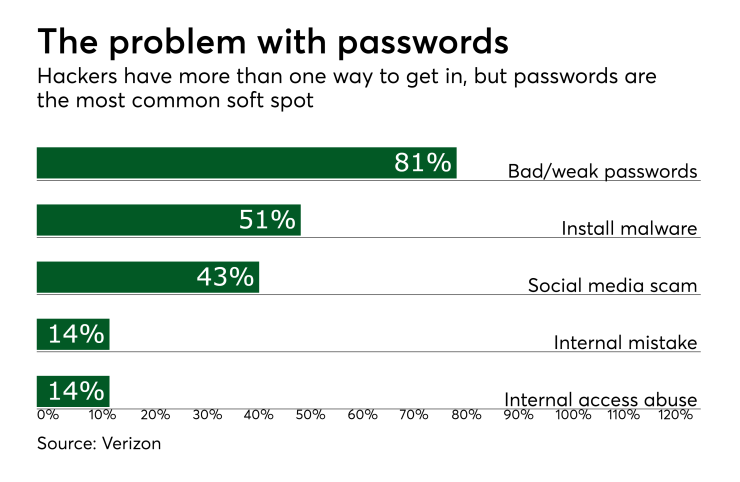
This breach underscores once again that mere reliance on passwords and usernames is insufficient to protect their organization and their customers from online fraud. It’s past time for every organization handling sensitive data to lock down their security, and to stop relying personally identifiable information to verify users — which is easily stolen and easily reused.
To protect consumers and companies from the fraud that can stem from a POS breach, companies transacting online need to change the paradigm. By implementing verification technologies such and passive biometrics and behavior analytics companies can verify customers beyond their credit card number, credentials, and any other data so they can be positively identified by their online behavior.
This increased authentication as part of a layered security framework allows retailers to block fraudulent transactions even if the right passwords, credit card numbers or security questions are used. It also allows them to correctly identify key customers to offer rewards, bonuses and more.





